Researchers looking to identify how pervasive the bug is found it present all the way back to the original commit for pkexe (commit c8c3d83 May 2009). It is easy to exploit locally and can allow an unprivileged user to gain root privileges. The exploit, according to Qualys is a memory corruption vulnerability, but it is instantly exploitable regardless of distro or architecture. It does not even require the Polkit daemon to be running to exploit. It is one of the types of exploits that gives security teams nightmares. The only thing that it does not have, at the moment, is a reliable method for remote exploitation.
PolKit, to oversimplify, is like Sudo for system. It allows unprivileged process to interact with privileged ones. It has additional functions that allow it to be used to launch privilege elevated commands via the pkexe process. According to Qualys,
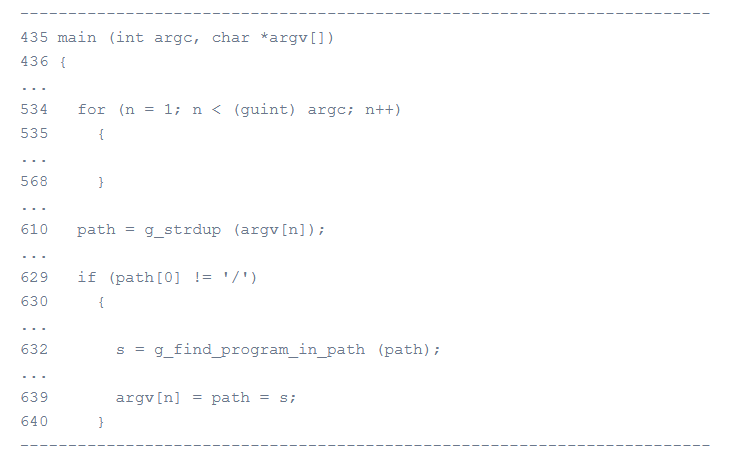
“The beginning of pkexec’s main() function processes the command-line arguments (lines 534-568), and searches for the program to be executed, if its path is not absolute, in the directories of the PATH environment variable (lines 610-640)”
“Unfortunately, if the number of command-line arguments argc is 0 – which means if the argument list argv that we pass to execve() is empty, i.e. {NULL} – then argv[0] is NULL. This is the argument list’s terminator.”
In the code we see that pkexe hard sets the integer n at 1 while also setting up our out-of-bounds read and writes for argv[1].
“If our PATH environment variable is “PATH=name”, and if the directory “name” exists (in the current working directory) and contains an executable file named “value”, then a pointer to the string “name/value” is written out-of-bounds to envp[0];”
In simpler terms by pushing a null value out-of-bounds it allows for an attacker to push an unsecure environment variable into pkexe’s environment.
Qualys first detected the vulnerability back in November 2021, but they waited until there was a patch available before disclosing (as is proper). The fact that his bug has been around since 2009 does mean that there is a likely hood that it has been used before and could be part of an existing APT’s tool kit after initial compromise of an environment. Although it is not remotely exploitable, if an attacker can login as an unprivileged user, they can quickly gain root via this vulnerability.
PwnKit is one of those rare vulnerabilities that rates a “patch of mitigate now” rating from just about everyone. You should be able to scan for it via the CVE number or reach out to your vulnerability scan vendor and find out of they have a specific out of band scanner for it available to help reduce potential false positives. Once identified you should check your distro to see if there is a patch. There should be for most distros at this stage. If there is not, Qualys has recommended a mitigations step.
“If no patches are available for your operating system, you can remove the SUID-bit from pkexec as a temporary mitigation; for example:
# chmod 0755 /usr/bin/pkexec”
As a footnote Qualys says that it is possible that both BSD and Solaris also contain this vulnerability although as of this writing they have not tested them. The mention that OpenBSD is not vulnerable as its kernel will not execve() a program is argc is equal to 0.
Happy patching.