Binarly disclosed the flaws to HP and CERT/CC teams as part of their responsible disclosure policy and have been working with them to identify methods to reduce the impact of them. This is the 2nd large release of vulnerabilities identified in UEFI subsystems this year (the first was in February). The flaws demonstrate something that we have been talking about since 2014 when we saw one of the first proof of concepts for UEFI persistent malware. Now, almost seven years later we are starting to see just how vulnerable this subsystem is and seeing more APT groups targeting it.
It has gotten bad enough that even government security agencies are talking about it with statements like “Securing the firmware layer is often overlooked, but it is a single point of failure in devices and is one of the stealthiest methods in which an attacker can compromise devices at scale,”. Because the UEFI firmware is responsible for initializing hardware and the loading the operating system it can inject payloads into system and kernel level processes. In most cases it can do this without worrying about anti-malware or EDR software installed on the device.
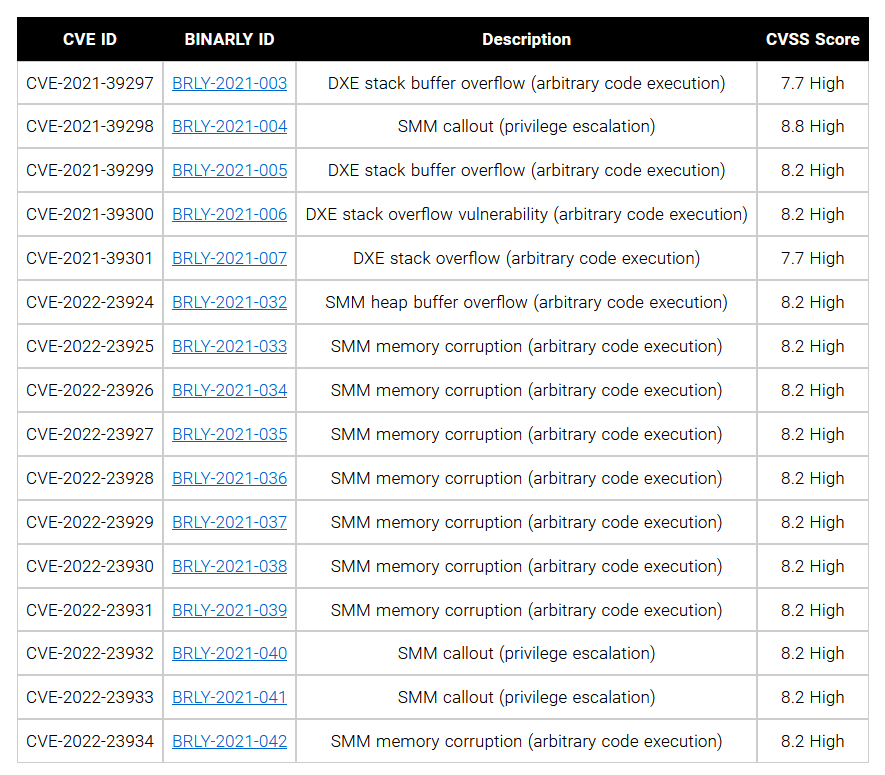
Looking over the list of disclosed vulnerabilities you can see just how many options an attacker has available to escalate privileges and execute arbitrary code on a device. It is more than a bit frightening from a security perspective. Still even with lists like this and the increasing concerns about UEFI attacks, there has not been much of a focus on protecting these critical pieces of the computer ecosystem. This area od security is largely left open and even when there are disclosures like this it can take months before actual updates/patches are available and even more time before they are applied. It leaves a wide part of the computer world vulnerable to attack and compromise at a very critical level.
According to Alex Matrosov, Founder and CEO for Binarly, “Binarly believes that the lack of a knowledge base of common firmware exploitation techniques and primitives related to UEFI firmware makes these failures repeatable for the entire industry. We are working hard to fill this gap by providing comprehensive technical details in our advisories. This knowledge base is crucial for developing effective mitigations and defense technologies for device security.” This statement is far too true than we would like given the modern threat landscape.
If you have an HP device, check to see if you have a UEFI update, if you do install it as soon as possible to avoid possible compromise.
Happy patching.