The investigation started when zscaler researchers noted many Microsoft Office files being submitted to services like Virus Total for investigation. These files turned out to be specifically crafted documents with political conflict themes relating to Palestine and Israel. The themes are what clued the zscaler researchers to the fact that Molerats was involved.
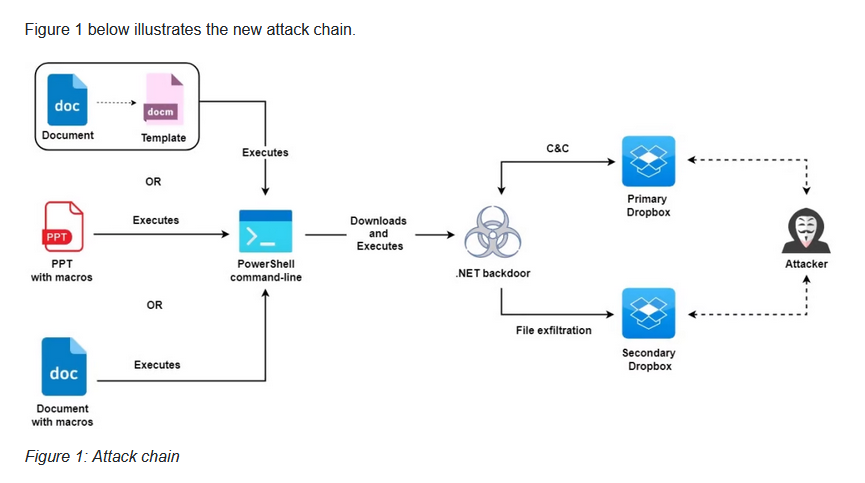
This campaign started in July of 21 with carefully chosen targets in the Palestinian banking sector, political parties, as well as human rights activist and journalist in Turkey. The attack, like many, use macros in Microsoft Office documents that are designed to engage the targeted user. The user clicks on the link which executes a PowerShell command to pull down a .NET based backdoor. This backdoor connects to two different dropbox accounts via the dropbox API. One is used for command and control, the other for data exfiltration. The .NET backdoor itself is obfuscated to look like WinRAR including the right icon and static resources directly from the legitimate version of WinRAR. The campaign’s goal is information collection. Once the target is compromised, the payload begins gathering information using various methods (including WMI calls and screenshots.
This type of attack again focuses on proper endpoint security. Having the right type of anti-malware combined with link and document security can help reduce the risk of infection by an attack like this. The use of both MS Office documents and potentially PDFs shows that this type of security is still lacking in far too many organizations.