When you go to a website like a bank or even your Gmail account your browser makes a subtle change to the way it communicates with those servers. It changes from the Open and insecure http (Hypertext Transport Protocol) to https (Secure Hypertext Transport Protocol) you can see this in the address bar on your browser. Simple right? Well there is more to the change than just that.
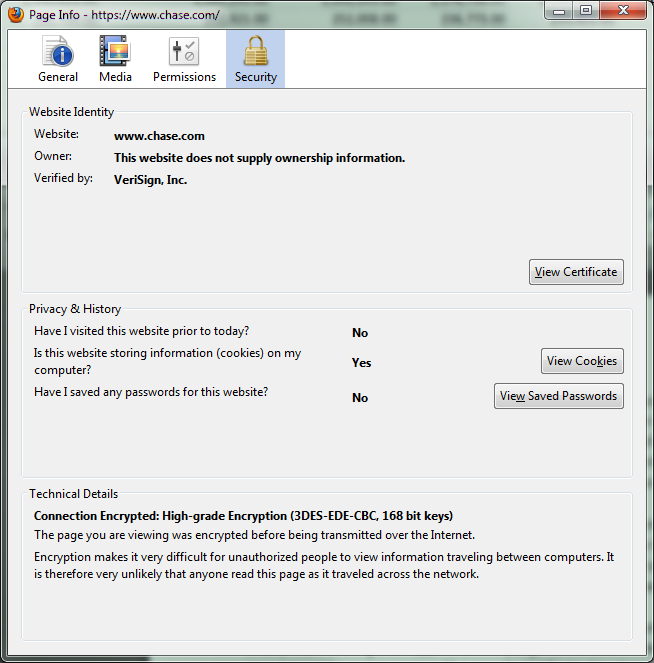 some certificate information on chase.com
some certificate information on chase.com
To keep things simple we will take a look at only a few steps in the process (and not necessarily in order). The first thing that happens before you get to the secure side of the site is the server responds to your request for secure access with a security certificate. Your browser is going to check a few things first. Now this certificate is used to validate the identity of the server you are contacting. Once that happens you change the way you are communicating with the server in question to a Secure Socket Layer (SSL) protocol and the ports also change from 80 for common web traffic to 443 for your SSL Tunnel. This SSL Tunnel is meant to allow for encrypted traffic between you and the server you are talking to. 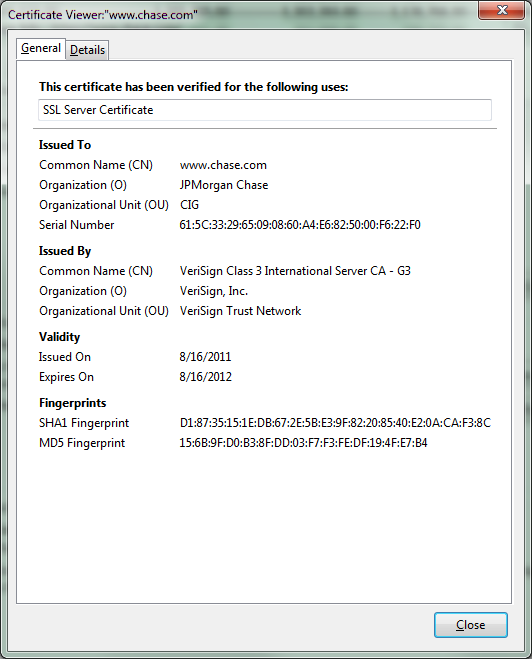
Here are your fingerprints for identification
Now all of this sounds great right? Well it is not you see the certificate that is used to validation is only as secure as the company that issued it. If that company is compromised in any way someone can issue their own certificates that will look identical to the real ones (because they are). This has actually happened on more than one occasion. Even the addition of an intermediate certificate (a second certificate to validate the certification authority) has not helped. So now something we have come to trust has been found to be insecure and open to attack.
So what is the cure? Well right now there is not one, but there is a suggestion that might help. It is a method for adding additional validation to the process. Right now you only validate the certificate with the issuing authority. Every OS has a list of the major Certificate Authorities, so the process is very simple (and easy to break). The new process would add what they are calling a notary validation to the mix. To put this simply a notary would be a third party witness to the validity of the certificate. When you hit a server and check its certificate it would randomly choose a notary for validation. Every certificate would need to contain at least three notary services for validation.
Now this sounds great right? Well it is a big step forward, but there are some catches to it. On the one hand by using the notary (which would contain a “copy” of the original public key and other certification information) you can get around simple faked or forged certificates. However, the problem arises from the fact that the SSL system has been compromised even deeper than that. We have seen SSL certificates that were actually issued by a trusted authority. This means that if someone can breach the actual services by someone like Verisign or Geotrust and issue a certificate using their system then all bets are off.
To put it plainly, security on the internet has a VERY long way to go. The problem is that the computer systems in the hand of malicious individuals and governments are becoming better at cracking security faster than the security on the internet is improving. When you think about it, most of your data is still being handled by hardware that is 10+ years old. In some places it is much older than that (I even saw a 12 year old Cisco Firewall/Gateway at one attorney’s office….). So new ideas like this are great, but the core issue is that ISPs all need to get together and find a way to upgrade their networks and security… and do it without robbing their customers. After all, we put the safety of our personal data in your hands every time we logon to a website and we pay you to make sure it is a stable environment it is about time you make it one…
Discuss this in our Forum

 The internet is not a safe and secure place (I know this is a HUGE surprise to everyone), but many do not know just how insecure the system is and how continued legislation to “make it more secure” is actually hurting. Although we could write a small novel about the dangers of allowing corporate interests and government officials who have no working knowledge of how the internet works to change things, we will concentrate on one issue here and one that many people do not even know is broken.
The internet is not a safe and secure place (I know this is a HUGE surprise to everyone), but many do not know just how insecure the system is and how continued legislation to “make it more secure” is actually hurting. Although we could write a small novel about the dangers of allowing corporate interests and government officials who have no working knowledge of how the internet works to change things, we will concentrate on one issue here and one that many people do not even know is broken.

