One thing that we do know is that psychologically it is important for corporations and the government to show Anonymous as malicious and or incompetent. If they can succeed in this we they hope to remove the current “Robin Hood” image that they have and limit the collective’s popularity. We actually warned of this type of behavior several months ago as we saw popularity for the group rising and an actual respect beginning to form in the minds of many Internet users (especially the ones that are concerned with Net Neutrality). Although not the first, the recent labeling of Anonymous as a terrorist organization by the NSA (followed by a claim that Anonymous might go after the national power grid) shows that there is an effort to pain the collective in a seriously bad light.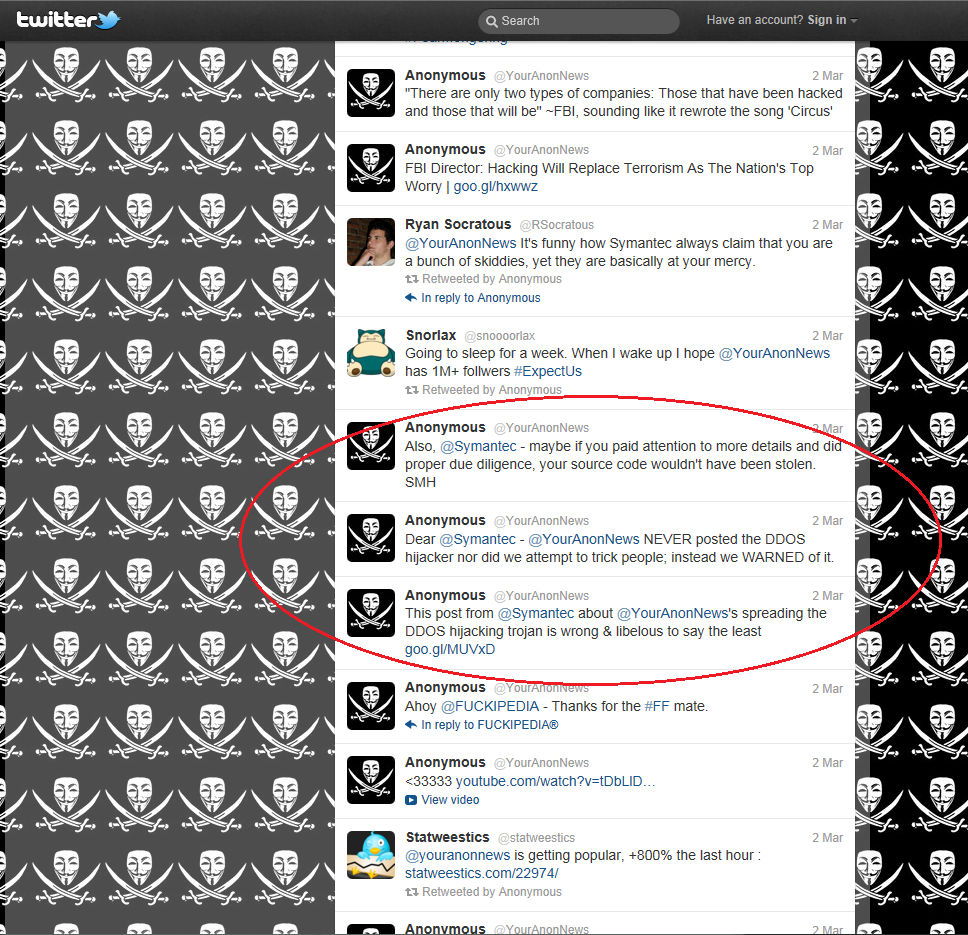
Now for the Symantec post; on the surface it looks very legitimate and with the inclusion of screen shots and a time line it is easy to see how this could have happened. They have screen shots showing an older pastebin link and also one they claim was posted by Anonymous with a link that contains a contaminated version of the tool Slowloris DDoS tool. The problem is that Anonymous members may have actually warned of the Trojan right after it was discovered. As the YourAnonNews feed has tens of thousands of tweets most people would not be willing to sort through them all to see if this was true, however… we decided to take the time and see if there was anything on this around the 20th (the date that Symantec claims the false link was setup). The search took over an hour, but in the end we got all the way down to the 7th of February before Twitter started to act up on us. A second and third attempt got us back to January 30th. This is very interesting, as it means that without serious searching Anonymous has no way to prove that they did warn people about the fake Slowloris tool (we are betting that Symantec either knew or was betting on this fact as well).
So now we have to wonder about the timing of Symantec’s release of this information. Why wait 30+ days to publish this if it is as important as they appear to claim in the blog? Or was the release timed to make it nearly impossible to find the original tweets? Looking at their own screen shot of searched tweets we noticed a few things that make us wonder. 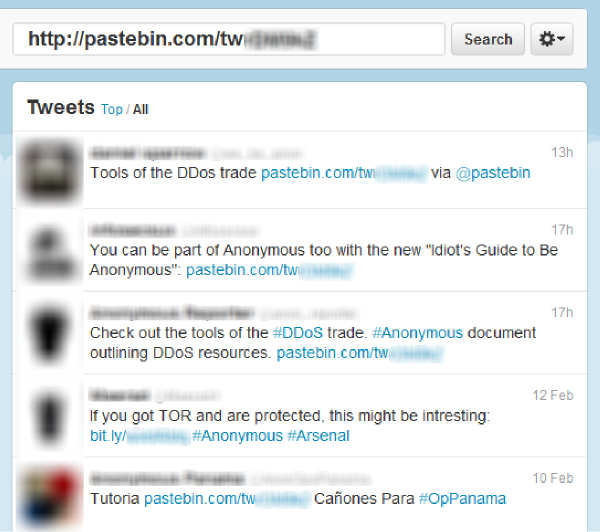
Why remove the avatars and names of supposed Anonymous tweets?
Why remove the entire last part of the infected link from the images?
How did the Tor Reference get in the search? (the link is not the same, that is a bit.ly link and does not match the alleged search string)
Symantec’s answer to the first one is going to be “to protect privacy”. The problem is that if these are really “Anonymous” tweets then their “privacy” is already protected. It would have actually been more damning to show their Avatar and User name instead of blurring it all out and claiming that it is Anonymous. Symantec did leave some avatars visible enough that you might draw a conclusion though (which is what they would like).
Symantec would also have an answer for the second question that would appear to make sense. They do not want anyone else to download the infected package. However, this logic also falls apart under close inspection. It would be more prudent to expose the link so that people know what to look for instead of hiding it so that others might stumble on it accidentally. After all it is only a like to the suspicious pastebin post and one that they claim is all over the place on twitter. However, by blocking the link they manage to create doubt and suspicion about ANY pastbin link that is supposed to lead to the Slowloris tool.
The last question we are pretty sure Symantec would not have an answer too. However, it is very odd that they included it. If you read both the fake and the alleged original pastebin screen shots you will see that both state “(PROXYS OR TOR ARE *NOT* SUITABLE)”. The TOR reference would be a giveaway that something is not right there. Searching through the YourAnonNews twitter feed we found several comments about Tor not being suitable for use in DDoS attacks. There are other mentions of Tor, but these are about how to use it and what it is intended for as well as information about TOR’s new masking system. Not once did we find tweets saying that you should use Tor for this type of attack.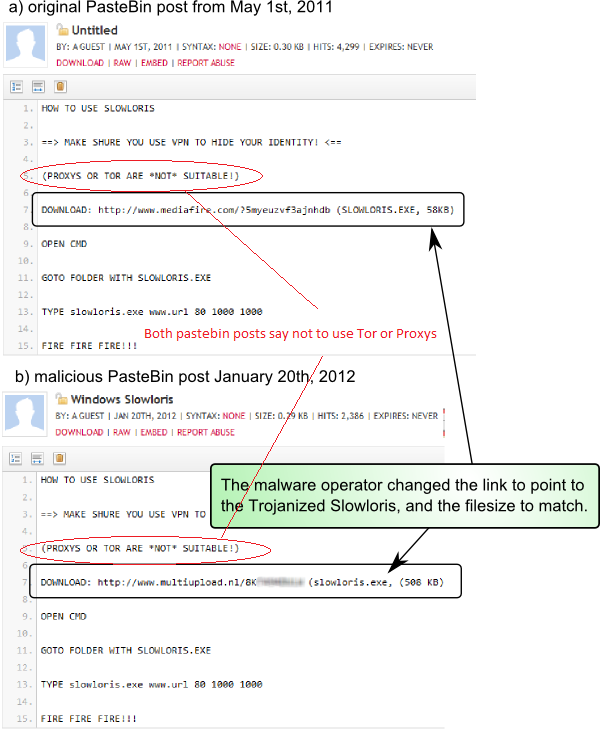
But there is more to this blog post by Symantec that meets the eye. The timing and psychology used is very important. On the one hand Symantec is releasing important information about malware injected into a tool commonly used for DDoS attacks and one that Anonymous has used frequently. However, the way they are presenting it is intended to so mistrust and fear. We would guess that their hope is to scare others that might be thinking of helping Anonymous in the future out of that course. 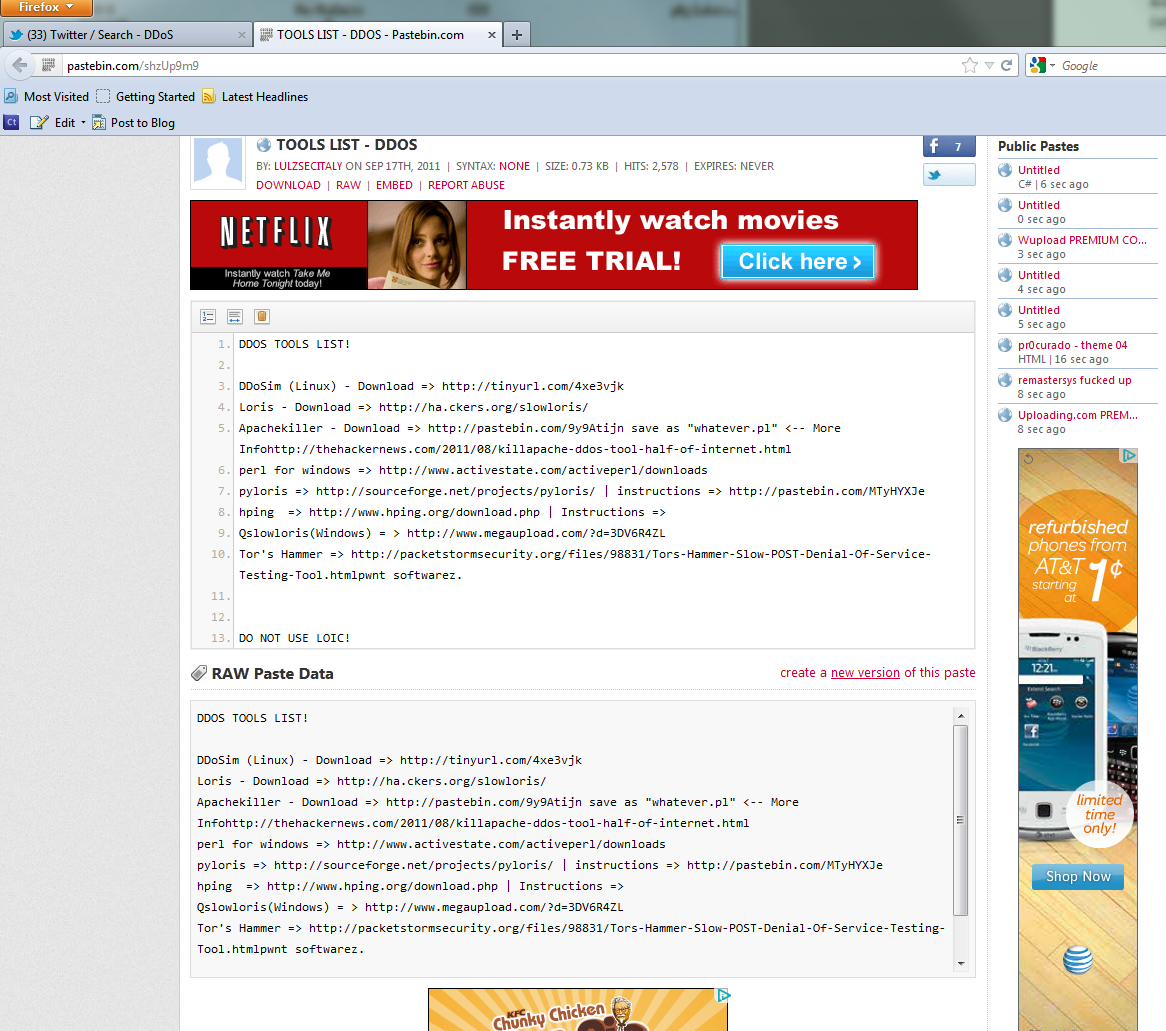
Another interesting thing, if you run a twitter search for DDoS you do find a single link to DDoS tools on patebin. Following the link takes you a pastebin post that dates back to September of 2011. This was put up by a twitter account called Anonymous Circle, not YourAnonNews (even though Symantec claims this in their timeline image). In fact after 10+ searches on Twitter for different terms we could not find any reference to YourAnonNews posting any links to DDoS tools at all.
In the end you have another attempt at sowing distrust and misinformation, but we would caution anyone about downloading anything unknown from the internet. That is just asking for trouble and if you do intend to grab tools from pastbin or other links you will want to make sure you run them through a serious virus scan before running them anyway. We have a feeling that we will see more blog posts like this (ones that make it impossible to find the original posts and with misinformation in them) as well as more attempts to make paint the online activist movement into a dangerous threat. Before you believe these stories, take a look around and then ask yourself “what is behind this and what do the original posters have to gain”. You might not like the answers you come up with.
Discuss this in our Forum
Editorials
Symantec Joins the NSA in Spreading FUD...
- Details
- By Sean Kalinich
- Hits: 7648
 Symantec, perhaps in an effort to reclaim some of their reputation, has released a report claiming that some people involved in the DDoS attacks after the MegaUpload take down may have been tricked into downloading a data stealing virus. In a post on Symantec’s own blog they have built a nice (and plausible) timeline of events complete with images (although no links) showing how this happened right around the 20th of January. Many news sites have picked this up and are busy wirting articles about how Anonymous has been hacked... Now the question is, is any of this true?
Symantec, perhaps in an effort to reclaim some of their reputation, has released a report claiming that some people involved in the DDoS attacks after the MegaUpload take down may have been tricked into downloading a data stealing virus. In a post on Symantec’s own blog they have built a nice (and plausible) timeline of events complete with images (although no links) showing how this happened right around the 20th of January. Many news sites have picked this up and are busy wirting articles about how Anonymous has been hacked... Now the question is, is any of this true?



