Yubikey is a product from the company Yubico. Yubico is a company that provides a range of security products to help increase online security. Yubico was founded in 2007 and provides a selection of hardware (tokens) and developer tools. We took a look at Yubico right after a series of hacks on companies such as GMail, LinkedIn, Yahoo and more. We went looking to see if there was any method to add extra security into these services even if they do not support it on their own. Yubico and Yubikey popped up at the top of the list. A quick click and we were on Yubico’s web page. Now prior to this we had never heard of Yubico before so seeing their offerings had us very curious. At the top of the list of products is the YubiKey. This is a One Time Password token that can be used to increase password security for a host of web based services. We contacted Yubico and after a short email exchange we have two in-house to test out; one is the standard Yubikey and the other is a new product called the Yubikey Nano. Now the interesting thing about Yubico and their products is that it is not entirely reliant on Yubico for authentication. Although by default the system does two-factor authentication against the Yubico servers (when using the proper plug in) you are not limited to utilizing their service. Yubico offers multiple development tools and internal servers to allow network admins to control their own authentication including a virtual appliance called YubiRADIUS.
At the top of the list of products is the YubiKey. This is a One Time Password token that can be used to increase password security for a host of web based services. We contacted Yubico and after a short email exchange we have two in-house to test out; one is the standard Yubikey and the other is a new product called the Yubikey Nano. Now the interesting thing about Yubico and their products is that it is not entirely reliant on Yubico for authentication. Although by default the system does two-factor authentication against the Yubico servers (when using the proper plug in) you are not limited to utilizing their service. Yubico offers multiple development tools and internal servers to allow network admins to control their own authentication including a virtual appliance called YubiRADIUS.
As with many products that we get in-house we wanted to see how well these devices work right out of the box. So we grabbed the Yubikey and set off to see if it really can let you take TFA security with you wherever you go. Our first test was to just validate the key worked at all. We plugged into our desktop and after the drivers (built-in HID drivers no others were needed) were installed we headed over to the Yubico website to verify that the key worked. After a simple test we found that the Yubikey worked exactly as described; you simply plug it in, wait for the green light and the press the light with your finger. The key will do the rest.
There is not much to the Yubikey; it is a small, lightweight USB key that has one purpose, to add an extra layer of security to password protection. As we mentioned we received the personal Yubikey which is tied into the Yubicloud TFA service. Each key is coded so that the Yubico servers (or a YubiRADIUS Server) can recognize and authenticate it. For most users this is going to be enough to work with as typically people want to find a way to secure their online accounts. Yubikey works well with online password manages like Lastpass, Password Safe, KeyPass and others. You can even integrate the Yubikey with an Enterprise Lastpass account making it very simple for a business to issue these keys and manage them. This means that you can use a much more secure method of getting to your stored passwords than just trying to remember one.
Yubikey works by generating a unique passcode each time you press the green light on the key or in the case of the Nano you touch the exposed metal part. This closes the contact and allows the Yubikey to send the unique passcode; the Yubikey will also complete the session so there is usually no need to click on login to finish. As the Yubikey shows up as a HID (Human Interface Device) it does not need any additional driver support and works on any device that supports a keyboard (that means tablets and phones too). From there the site confirms this passcode against what it should be on the Yubicloud servers and if there is a match you get access. Developers you can install a plug-in or hard code access to the Yubicloud through their website. This allows you to establish solid TFA for your site and to give greater security to your users.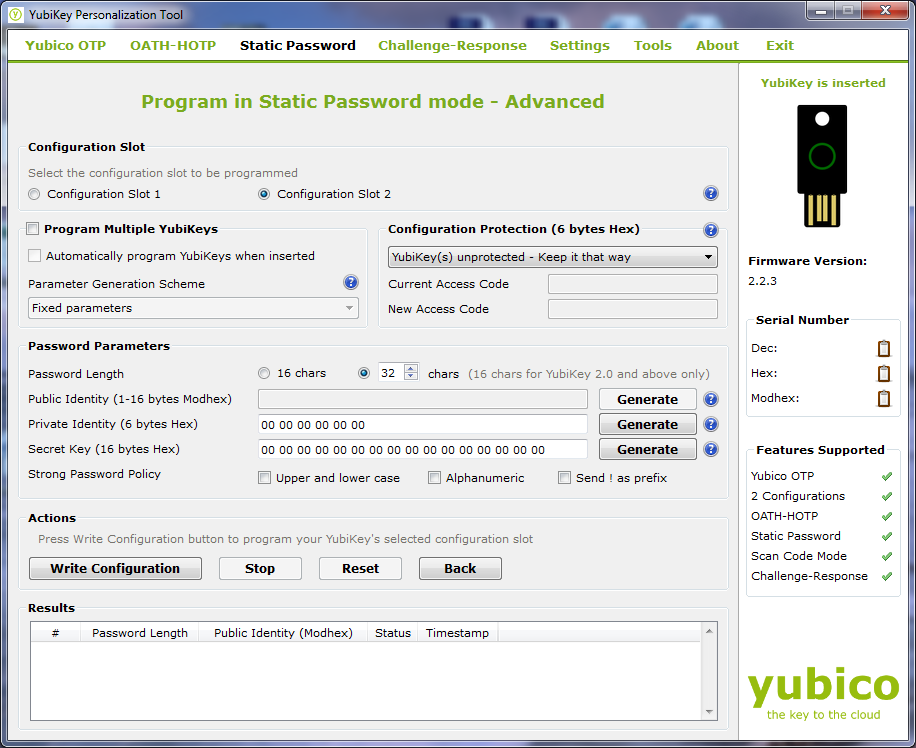
For sites that are not Yubicloud enabled you can setup a second ID inside every Yubikey with a static password. This can allow you to create a password that is complex without the need to remember it. This extra feature allows the Yubikey to provide multiple levels of security to your online accounts. You can still maintain the OTP (one time password) for sites that support Yubikey and have a complex password for services that do not have Yubikey support. You can grab the tool that lets you configure the static password from Yubico’s website (they have one for just about any OS) along with multiple tutorials on how to use it properly. If you are considering using the Static password option it is important to remember that it is still susceptible to some keyloggers as the information is still passed to the input box on the website or form. You will still want to keep your system free of malware and viruses. The static password can also be typed out in word or notepad if it is open making it simple to compromise if someone can get access to it even briefly. For the OTP there is no way to pull the algorithm out as the memory on the device is write-only. There is probably a way to get it off the key, but that would require physical access to the key and at that point you have bigger issues.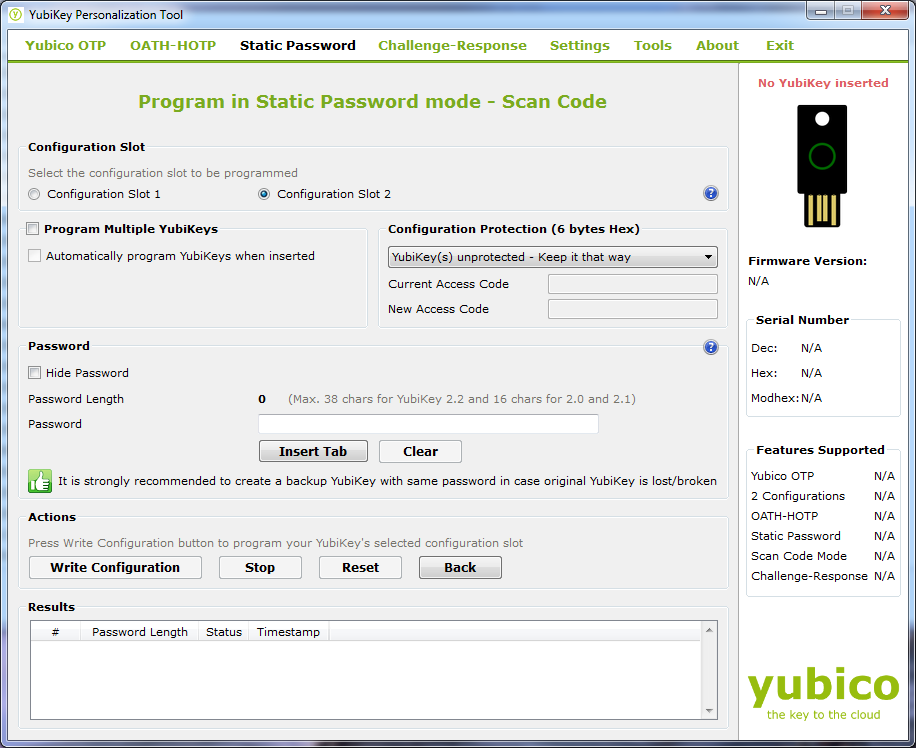
Even after a few days of use we are very impressed with what this little key can do to help you improve your online security. You can configure OTP, Open Authentication OTP, Static (complex) password support, challenge and response multiple configurations and even more. We did run into a small snag with programing the dual configurations. The documentation for this is not the best and it took us about 3 hours to get it going. If you are running dual configuration especially static and OTP you will need to use the advanced mode for programing. There is nothing that tells you this, but in the end it was the only way we got it working. You will also need to be aware that each configuration has a certain “press” that enables it. A simple tap (0.3 to 1.5 seconds) will get you configuration one while a longer press and release (between 2.5 and 5 seconds) will kick off configuration 2. Yubico also offers a method to completely revoke a key in the event that it becomes lost or stolen. It is a simple setup and gives you even more flexibility over your accounts and how you access them. If you pick up a Yubikey, setting up a YubiRevoke account should be the first thing you do.
There is quite a bit more that can be done with the Yubikey and other Yubico products. So far we have only nicked the surface of this product and its usage. We will be diving deeper into options for the enterprise, use with Open Auth (OAUTH-OTP) , configurations for secure VPN use (with YubiRADIUS) and even how to reprogram your Yubi with a new AES key. For now we can certainly recommend the Yubikey for sites that support it and also to allow you to use complex passwords with your online accounts (using the dual configuration mode).
Discuss this in our Forum




