Still will enabling two factor authentication really do any good and what are the drawbacks that prevent people from using this extra layer of security? We should probably explain what two factor authentication is for anyone that does not know. Simply put two-factor authentication (we will call it T-FA moving forward) is a security process which requires two means of identification, one of which is typically a physical token, such as a card, and the other of which is typically something memorized, such as a security code. In authentication there are three common factors for authentication they are typically broken into the following terms: something the user knows, something the user has, and something the user is.
In banking the two factors are something you have (your debit or credit card) and something you know (the PIN you memorized). In many higher levels of VPN encryption the factors are something you are (your login information /username and password) and something you know (a counter token generated by a security fob). Unfortunately both of these styles of T-FA are vulnerable to attack and also to breach through user carelessness. With the typical banking PIN the number is only 4-digits which limits the number of possibilities, but most banks have caught onto that and will invalidate the cards after a limited number of failed attempts. With the use of token generators we have seen them breached with man-in-the-middle attacks and also due to poor number random number generation patterns. There are some that feel this is how Diablo accounts using their T-FA are being compromised, but there is no concrete proof of this from Blizzard.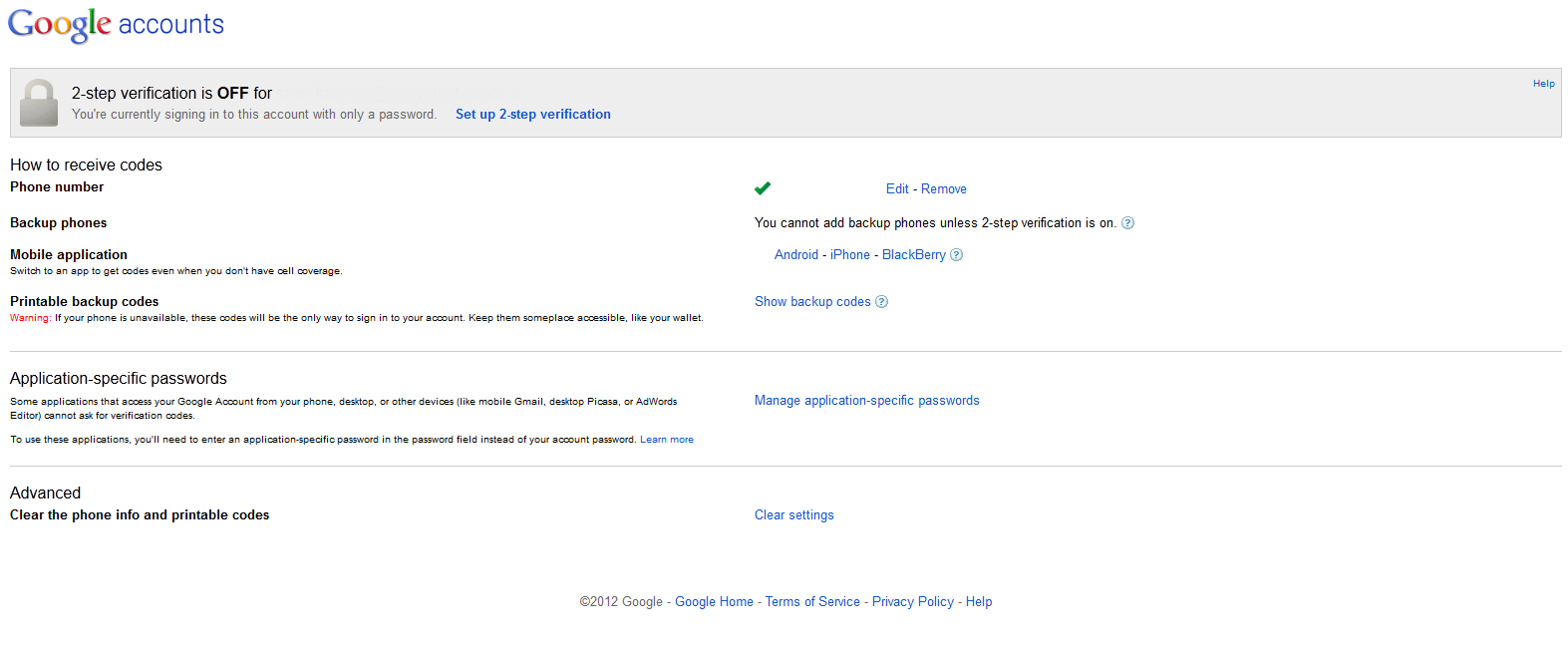
With Google services the method for T-FA is much simpler and also potentially much easier to breach. When you enable T-FA you have a couple of choices, you can have Google text you the code to one or more phones, get a random code from an app on your phone (Android, iOS, Blackberry) and you can even print backup codes in case you no longer have access to any of the other options. These cover a wide variety of options and seem to allow the best security.
Unfortunately as Google points out there are many applications and devices that cannot ask for a T-FA token so they are still vulnerable. Mobile devices like your iPhone, Android Phone and Blackberry are among them. This means that you have to setup a special password for these and type it in right away to make sure your phone can still access the information you want/need. Still getting TF-A (Google calls it 2-step authentication) is easy and fast. So why do people not use it?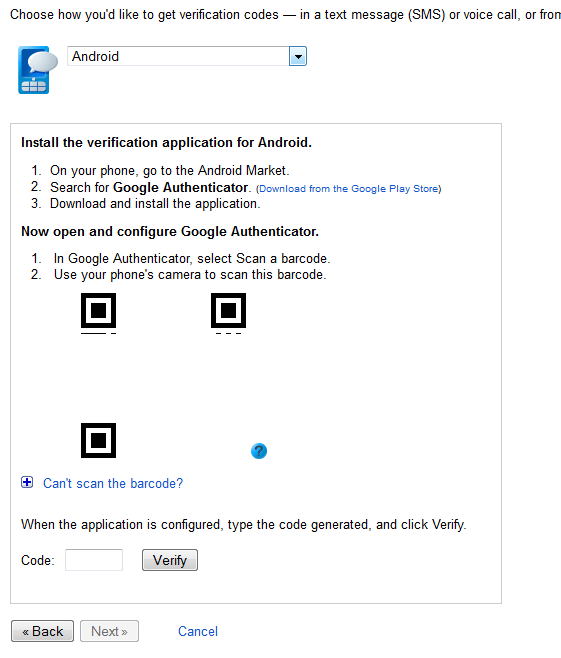
Sadly any real security measure will take away speed and convince. Forcing complex passwords makes it harder for people to remember them; requiring password changes makes employees annoyed at you because they usually are still having trouble remembering the last one. I can remember visiting a client who was upset because the receptionist’s computer kept getting viruses. They asked me to check it and see if she was visiting sites she should not have been. After cleaning the system out I checked the history and found that someone was online at some very inappropriate sites, but at 11PM. A quick check showed that the person doing it was logging in properly as well. When I asked if they were still using the complex passwords and password expiration I set up they said yes. I went to log in using the receptionists account she pulled a piece of paper from an unlocked drawer with the words “new password” on it and then typed in her password into the computer. You would be surprised at how often this happens.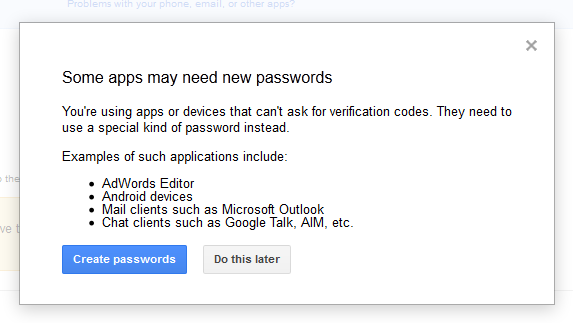
The same can be said for requiring a token. Again with a client we setup a nice VPN system that required the password to be different from their Windows Login and used an RSA token for access. About a month later we got a call asking us to check on this as the suspected a breach. In the end we found out that the CEO asked for his login to match his Windows information so he would not have to remember two passwords and four people had lost their tokens. All of the security put in place was too much of a hassle for these people to use. This is the same thing that people using services like Gmail, iCloud or any other cloud based service do. After all they are using these services for their convenience, not for security. They expect Apple, Google, Microsoft, Amazon and any other company to take care of security.
Security is far too often overlooked by both the end user and the service provider until it is too late. We know that using T-FA can save you in the event of a casual breach and highly recommend it, but the problem is that many people will get annoyed with it quickly and turn it off. They want to quickly login and do their thing, they do not want to type in multiple passwords or pin codes just to check email. No amount of recommending by Google, Apple, or anyone is going to change that. Google and others know this or they would have made it a requirement by now. The reason they do not is they know that many people would leave for services that are not as complicated and that is something that they just do not want.
Discuss this in our Forum

