Normally we would never be promoting a browser developed by and that comes default in a Microsoft operating system. However, recent developments and announcements from the purveyors of the big blue E might change our minds. The change comes from a shift in how Microsoft viewed their browser and the vulnerabilities in it. We have said for a long time that if all you are doing is chasing numbers, you are not going anywhere. Instead, you need to look at risk from an attacker perspective and remove the toys they want to play with. This seems to be what Microsoft has done.
In November 21 Microsoft added in a new Enhanced Browsing mode (Balanced and Strict) for Edge under security settings. The Strict setting disables JIT (Just-In-Time) compilation from the processing pipeline. Given the number of exploits that target this feature it can have a massive effect on the security of your browser. It can also break legitimate sites, so there is a tradeoff. If you do not mind manually adding sites that you need to interact with, well the things are all good. Balanced also disables JIT, but it tracks the sites you visit and adapts the security posture based on that interaction. Both options also enable Intel’s Control-Flow Enforcement Technology that adds extra exploit mitigation at the hardware level.
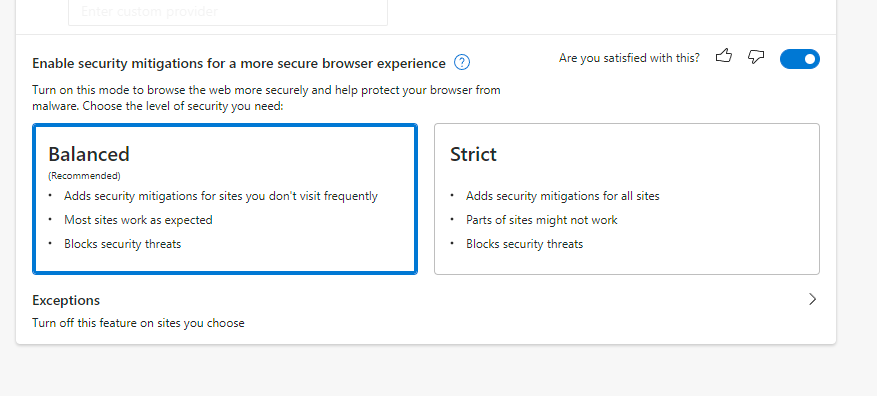 |
Domain admins will enjoy knowing that this new mode can be set and adjusted thought Group Policy. This will make enforcing these security options easier across domain owned assets. For BYOD systems things will be a little more complicated, but we hope that you have a good BYOD policy to cover the enforcement of organization security standards in place (along with good security tools). Pushing Edge with the strict mode on via Intune is also an option for MS365 users (which is nice). These options also work in Windows, MacOS (just in time for the Safari15 bug), and Linux.
Now Microsoft is looking to add to those protections with Content Flow Guard, Active Code Guard, and a hardware level Stack Protection. These new features are current in Edge Beta build 98.0.1108.23, which was announced on the 14th of January. It adds in even more protections from zero-day attacks at the browser level at least.
Whether you love or loath Microsoft, at least they are trying to truly find ways to secure their browser. Maybe in the future, Edge will be used for more than just a method to get another browser downloaded…

