However, there is more to FUD than just name calling and a few poorly worded articles that spread around the news sites. There are subtle items that begin to erode trust and to villainize the movement at a more personal level. Symantec tried to capitalize on one of these with their Blog post claiming that Anonymous (the collective) had released a malware infected DDoS (Distributed Denial of Service) tool. We covered this story in some detail and found quite a few holes in it.
Now there is another piece of software with the Anonymous name that was making its rounds around the internet until the Open Source download site SourcForge pulled it. This was the improperly named Anonymous-OS. There were multiple things that queued SourceForge to the fact that this was a bad thing. The first was the fact that the project group had already claimed they were not affiliated with the larger collective. This should have sent warning bells going as it reeks of capitalizing on the current buzz around the Anonymous movement.
The second was the multiple comments that the OS and software had malware pre-planted inside. After that Anonymous (the collective) warned people against downloading it as they said it was fake and full of Trojans. In the end SourceForge did the right thing and pulled it. However, even by pulling the OS it has sparked much talk on the internet with misleading headlines and now stands as the second time someone has attempted to use the popularity of the Anonymous movement to spread malware. Whether these are attempts to discredit the group, attempts to profit from the unwary, or both is not clear. 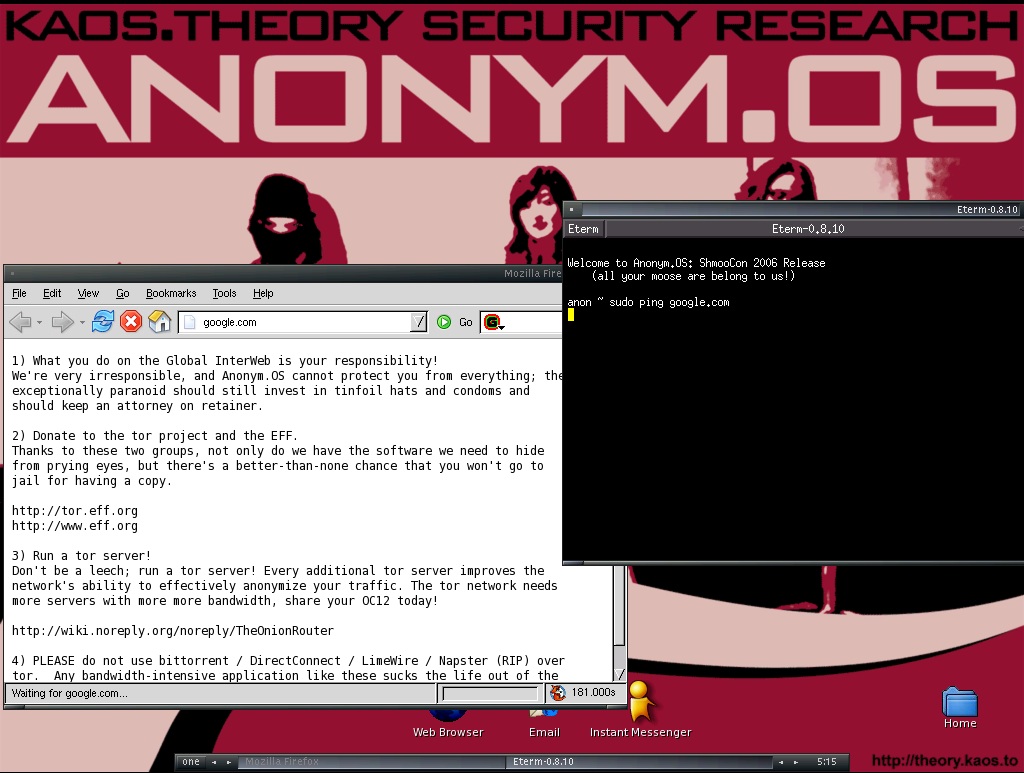
There have been operating systems that offer anonymity going back for years. One of the first and most crude was simply a Linux Live CD with Tor on it. The Live CD runs in active memory space and not from your HDD. After a while people began to write their own Live CDs that incorporated Tor and other tools to harden the OS. There was a project called Phantomix which was based off of Knoppix and that incorporated both Tor and Privoxy. After that we saw multiple builds and live CDs that built on the same concept as Phantomix most of these were useless for more than about a month as both the Linux Distro they were on and Tor update constantly to adjust to security, privacy and other general usage items. One of the most famous or perhaps infamous was the Anonym.OS. This was put out by Kaos.theory security and research (Dr. Kaos and others). Kaos.theory also created NARC (Network Analysis Reporting Console) and SAMAEL (Secure, Anonymous, Megalomaniacal, Autonomous, Encrypting, Linux). The SAMAEL project was a server based system that bundled what you got with Anonym.OS and added much more to the mix. Both of these projects happened back in 2006-2007 and at the time were very popular and with the exception of SAMAEL (which never did get released) they are still available online just not in any current format.
However if you are looking for an Anonymizing operating system and want to go the live CD (or USB) route we would recommend using Tor’s Trails system. This is your best bet for both anonymity and security (they will not have Malware in theirs). Plus, let’s be honest, if you are looking for anonymizing tools you will probably start things off on the Tor Project’s website and ignore what is only the first of many attempts to profit on the popularity of the Anonymous movement. Just remember that Tor does not guarantee protection from observation. Just like the regular internet there are honey pots, DNS to worry about (your request still go through standard DNS servers unless you take precuations) and more. Unless you have something like the fabled SAMAEL or other means of hiding your traffic on the Internet you are still partially visible when ever you use the internet.
Discuss this in our Forum.
News
Anonymous-OS Turns out to be another attempt to capitalize on the popularity of the "real" Anonymous
- Details
- By Sean Kalinich
- Hits: 5087
 FUD (Fear Uncertainty and Doubt) comes in many forms. The most common is through the use of the News (printed and internet) here as hundreds of millions of people consume content from multiple sources the seeds of misinformation can be sewn with relative ease. Over the past few months we have seen the NSA, the FBI, Fox News, Symantec and others start to pain the Anonymous (and other) online movement as villains. The FBI, CIA and NSA have even begun the campaign to throw them into the same category as terrorists. Most of these have not met with success as more and more people are beginning to read between the lines of the daily news, but it still has an impact.
FUD (Fear Uncertainty and Doubt) comes in many forms. The most common is through the use of the News (printed and internet) here as hundreds of millions of people consume content from multiple sources the seeds of misinformation can be sewn with relative ease. Over the past few months we have seen the NSA, the FBI, Fox News, Symantec and others start to pain the Anonymous (and other) online movement as villains. The FBI, CIA and NSA have even begun the campaign to throw them into the same category as terrorists. Most of these have not met with success as more and more people are beginning to read between the lines of the daily news, but it still has an impact.



