This brings us to IZON. IZON is made by Stem Innovation, LLC and marketed to the connected crowd. It is one of those IP cameras that is designed to be reached via the cloud (using an iPhone) for easy monitoring by anyone… That last part is the problem. According to recent security research the IZON is very open to access (including configuration) by malicious individuals.
At least that is the case according to Mark Stanislav at Duo Security. He took the time to dig into a one of the IZON devices because it showed up on a NMAP scan of his network and the results were a little frightening. Sitting inside of his network was a device with telnet, http, RTSP (real time streaming protocol), and more open to anyone else on the network.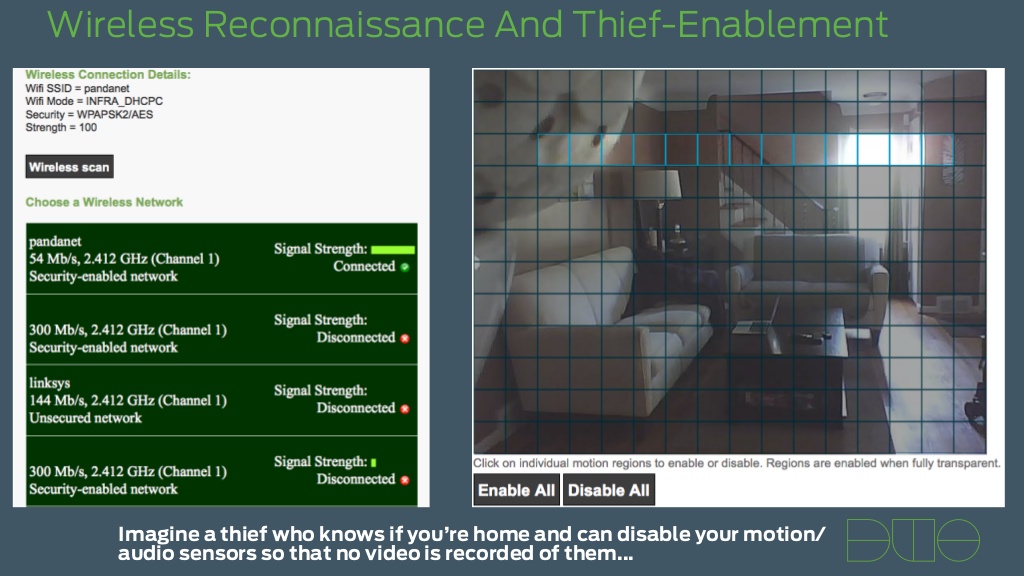
Now like any good security researcher he dove deep into the device just to see exactly how open it was and what he found was quite disturbing. As with other IP cameras out there, the thought that someone can connect and watch you and your family without any effort is a disturbing one. When you think about it a number of devices offer the ability to connect to your camera using your phone or other mobile device. The question is, how do they arrange this connection and are these setups secure at all? In the case of the IZON, the answer is not good.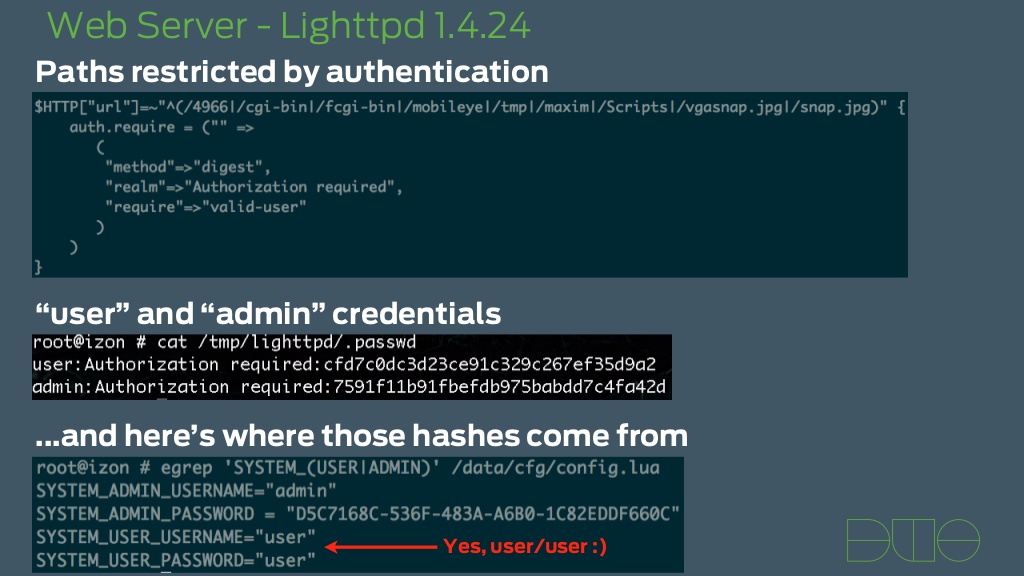
In order to find out what was going on behind the scenes Mark looked at the initial setup process and found that an encrypted password is sent during setup and used for connections from the app to the camera. He was able to dump the memory of the app to try and find the credentials. When this was done he not only found root credentials hardcoded into the app he also found another account that gave access to a hidden webpage. This is where things get scary. Unlike many other camera by-passes where you need to use a user agent string just to view the streaming video, on the IZON you can get to a page that lets you actually change settings in the camera.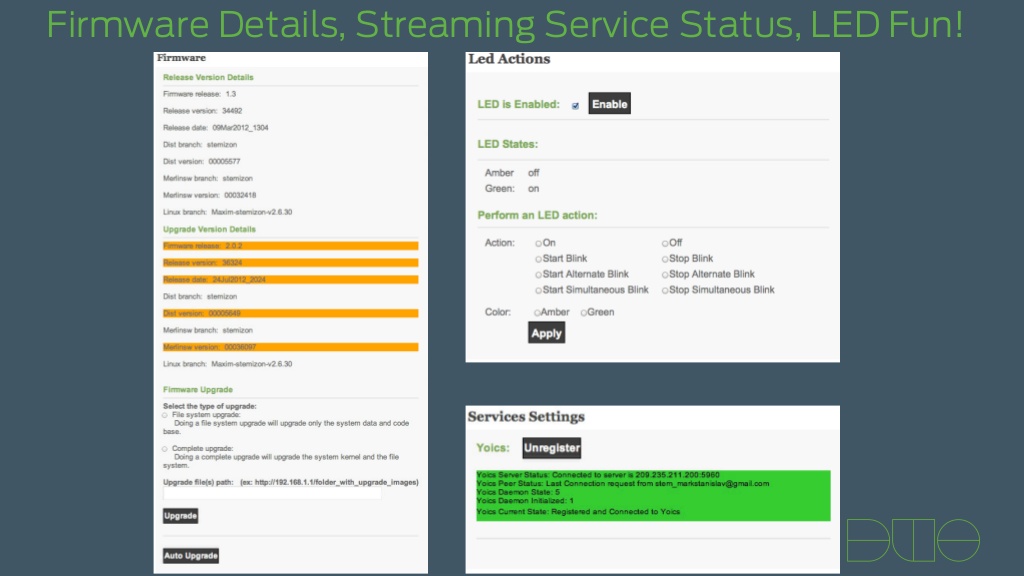
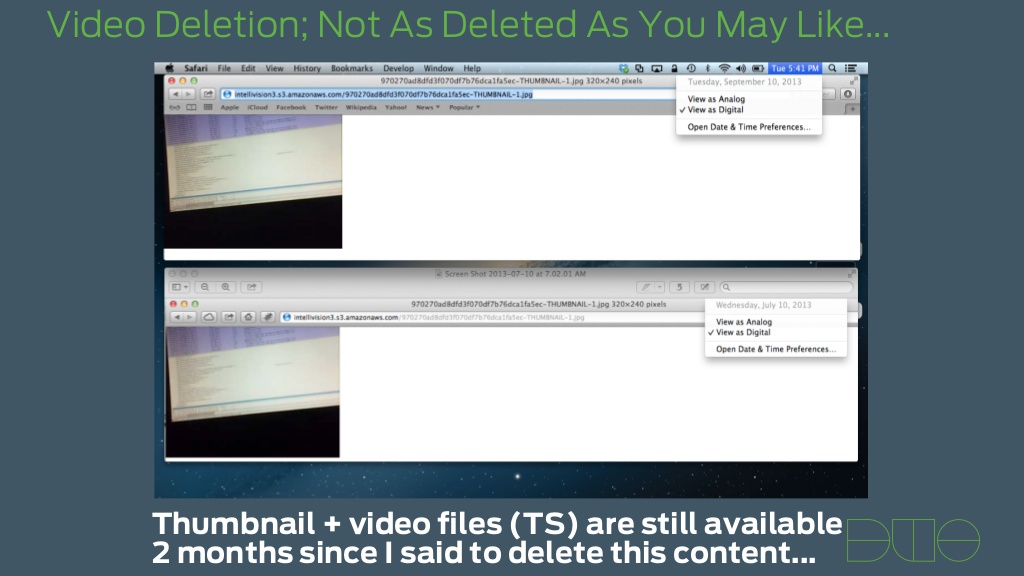
On top of these items the IZON is a cloud camera. This means that when you setup the system it connects to a service on the web for use in monitoring video streams and still images. There are two systems that are used for this; one is YOCIS and the other is intelli-vision. Both have user information exposed in the configuration and both have their own security flaws. With intelli-vision images and video were not removed from their servers even after they were supposed to be deleted.
 |
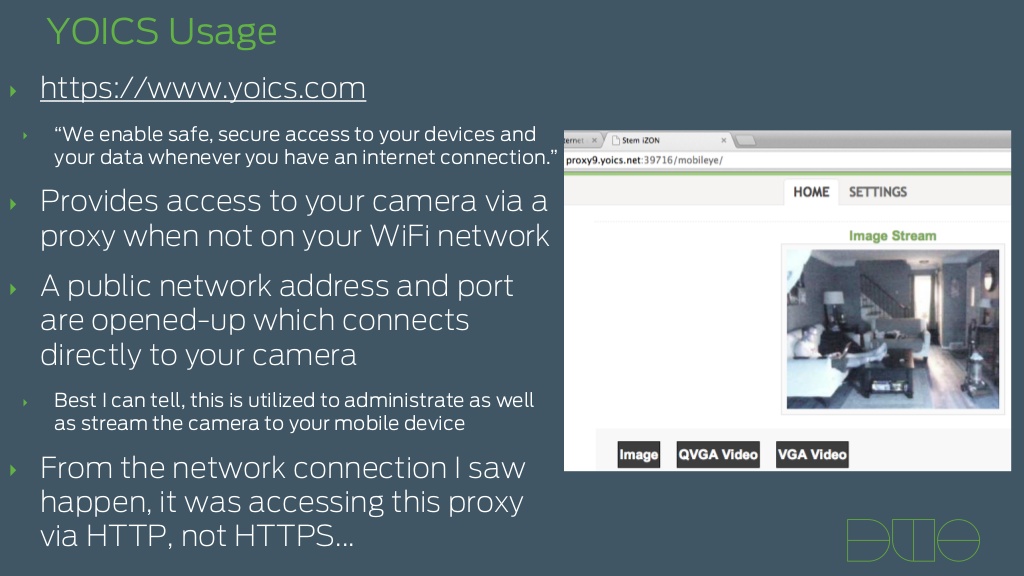 |
All-in-all the information that Mark Stanislav put together about the IZON is pretty disturbing. In many ways this is much worse than what we saw with TRENDNet and shows very clearly that many embedded devices have these flaws built right in. This is everything including printers, IP cameras, refrigerators, pace makers, routers, and even toilets. Like we said, the FTC sent out a strongly worded statement about TRENDNet and the issue they had (which was and still is bad). Perhaps they should have simply listed every company that produces a device with an embedded OS.
You can see the who slide presentation below:
tell us what you think in our Forum



