In May of this year a campaign was discovered that was targeting webservers with an aggressive password guessing attack. The attack is so aggressive that it actually set off DDoS mitigation schemes. We saw the effects of this back then, but as it was not a wide spread attack it was written off as a targeted attack on DecryptedTech originating in Russia. However, now that other hosts are seeing the same patterns a much wider investigation was started. Arbor Networks now says they have found six command and control servers that are controlling over 6,000 WordPress, Joomla, Datalife Engine CMS installations. On top of this, these six C&C servers also control an estimated 25,000 Windows Servers.
The attack is fairly simple and replies on compromised systems to do most of the heavy lifting. Once a system is infected it reaches out to different webservers running Joomla, WordPress of Datalife Engine. From there it tries a brute force attack using simple login and password routines (admin, administrator etc.). Once it identifies the correct combination it then installs a payload on the web server (or CMS installation) this payload gives the ability to browse the file system, transfer files (up and down) and also to execute commands on the server.
There is good news though as this campaign (called Fort Disco) is only looking for site with weak passwords as the password list that is used is only about 1,000 entries. Some of the top passwords scavenged by Fort Disco are shown below.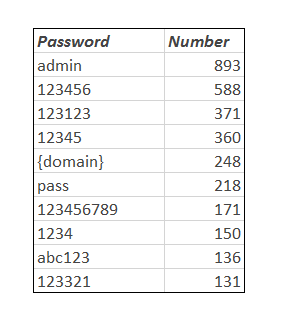
As you can see many of the targets are using passwords that are laughable in their simplicity. It hammers home the point that everyone needs to be concerned about password security and to also view even the smallest of personal blogs as a potential target (possibly even more so). Right now no one seems to know why these sites are being targeted and compromised. It is possible they will be used to spread additional malware or that they are just portals in an attempt to infect the larger host that contains the site. Either is a possibility and one that should be of concern. We wonder if this will make CMS developers change their software to require strong passwords during installations, or that they will work with two factor authentication (TFA) services like Yubico to add this option for administrative user. Either would be a good thing in the long run. For now, if you do not already have it we would recommend looking into setting up TFA for your CMS. There are several already on the market and most of them are simple to install and easy to use.
Tell us what you think in our Forum




