Kaspersky believes that Flame is not the work of Hacktivists or Cybercriminals instead the design, infected region and even the data it is
collecting all point to sponsored act. Exactly who is sponsoring this no one knows, but it is felt that it could be the same people that sponsored the Stuxnet and DuQu attacks. Between 2009 and 2010 Stuxnet was used to cripple Iran’s nuclear program, while DuQu was used as an intelligence gathering too looking to data on internal computer systems.
As an application Flame appears to be design for long term operations as it has plug-ins that can be swapped in and out to provide the functionality desired. Right now Kaspersky says that Flame is capable of recording screenshots, keystrokes, voice conversations (if there is a microphone attached) and scavenging data off of the infected system or connected network resources. With all of the plug-ins installed the malware is 20MB in size which makes the length of time it remained undetected unusual.
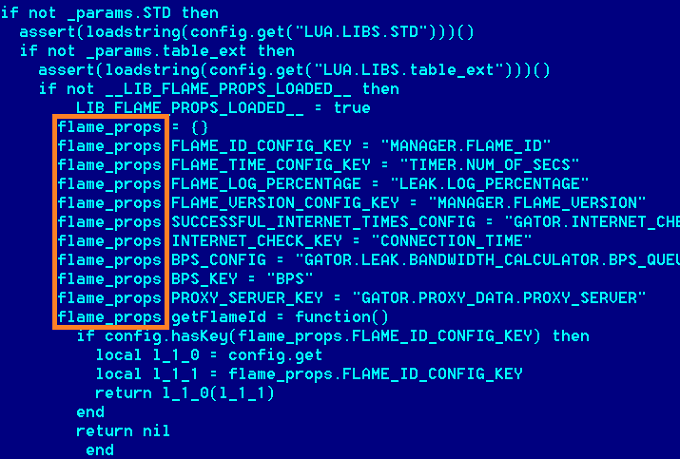
The attack looks to be one of the most complex ever identified and is something that may take years to completely break down. The developers appeared to try and actually hide the malware through the use of an advanced scripting language (LUA) that can be extended to the C programing language. According to the securelist blog;
First of all, usage of LUA in malware is uncommon. The same goes for the rather large size of this attack toolkit. Generally, modern malware is small and written in really compact programming languages, which make it easy to hide. The practice of concealment through large amounts of code is one of the specific new features in Flame.
"The recording of audio data from the internal microphone is also rather new. Of course, other malware exists which can record audio, but key here is Flame’s completeness - the ability to steal data in so many different ways.
Another curious feature of Flame is its use of Bluetooth devices. When Bluetooth is available and the corresponding option is turned on in the configuration block, it collects information about discoverable devices near the infected machine. Depending on the configuration, it can also turn the infected machine into a beacon, and make it discoverable via Bluetooth and provide general information about the malware status encoded in the device information."
As you can see this bit of malware is as impressive as it is frightening. The question is now; who developed this and was it all part of a three pronged attack? Stuxnet and DuQu used some of the same source code while Flame appears to be from different minds entirely, but there appear to be indicators (geographical region, targets, methods of transmission) that make some feel they were all part of the same attack. There is also some evidence that Flame may have been around in some form since 2007.
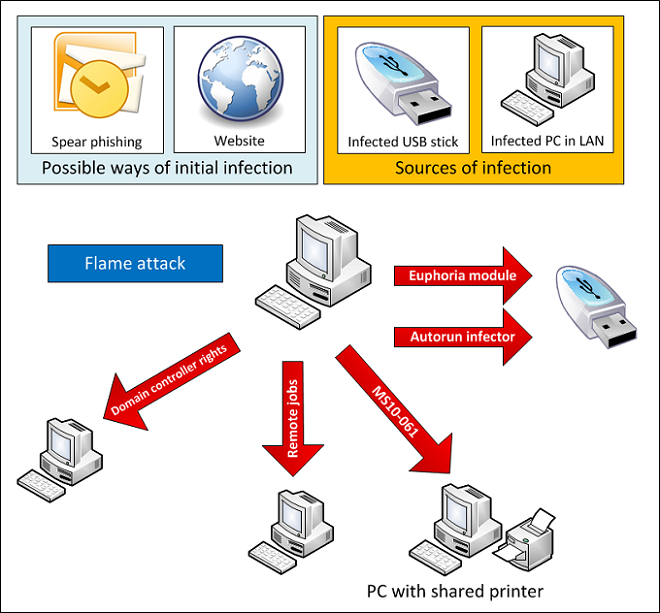
The means of infection appears to be through infected USB sticks and also through LAN connected systems that are already infected. Researchers also know that due to the large size of Flame it is installed in multiple parts. There are probably other methods of infection and there is also a good chance that Flame is using one or more 0-day vulnerabilities as it has been observed infecting a full patched version of Windows 7. In all this attack is of serious concern due to the complexity of the code, the command structure (commands can be set to completely remove all traces of the malware) and the C&C structure. Right now there are approximately 80 domains used to communicate back to the C&C servers. This can make identifying them difficult at best.
Kaspersky has just begun their investigation into Flame so we are sure more information will be forth coming about what it does and perhaps why, but without the who it remains a threat and one we are sure that will have some people losing sleep at night.
Discuss this in our Forum

 An interesting report has popped up about a rather large attack on a group of Middle Eastern countries. The attack (called Flame) appears to be a targeted attack against Iran, Israel, Palestine, Sudan, Syria, Lebanon, Saudi Arabia and Egypt with the most effected being Iran, Palestine, and Israel. The attack was reported by Kaspersky Labs and looks to be intended to collect all kinds of information (not just data on computers). Kaspersky believes that Flame has been operating for at least two years in this region.
An interesting report has popped up about a rather large attack on a group of Middle Eastern countries. The attack (called Flame) appears to be a targeted attack against Iran, Israel, Palestine, Sudan, Syria, Lebanon, Saudi Arabia and Egypt with the most effected being Iran, Palestine, and Israel. The attack was reported by Kaspersky Labs and looks to be intended to collect all kinds of information (not just data on computers). Kaspersky believes that Flame has been operating for at least two years in this region.

