So now that you understand what USSD is you can see how easy is to do some serious harm with this hack. Users will be able to see the process going but won’t be able to do anything to stop it. If they get it from QR codes or NFC there will be no warning about it. However if you don’t have a Samsung phone with Touchwiz you are pretty much safe, as it will only show the code in the dial pad on other Android based devices. The problem with Samsung is that it does the dialing automatically.
Even though losing all your data is very unpleasant, you can somehow recover from it, but what brings real concern is the codes that kill the SIM inside the device. So be careful with scanning QR codes or using any NFC reader software, also if you have a Samsung phone, be sure to deactivate automatic site loading in those programs. TeamAndIRC tweeted that this vulnerability have been patched in i747 and i9300 firmware, but no official announcement from Samsung has been made. So if you have older firmware be sure to update, or pay additional attention to what links will you click. Also since this patch has not been confirmed the same warning applies even if you update.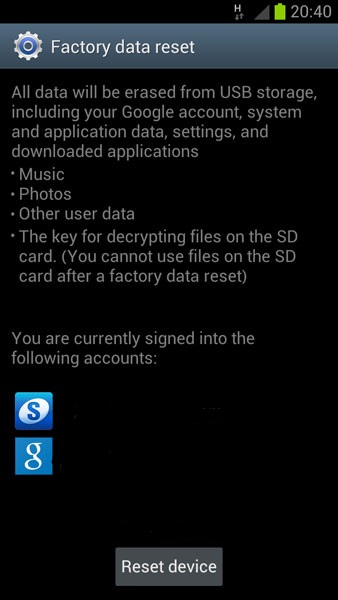
[Ed – This flaw is a serious one, but the interesting thing is that it affects GSM phones (USSD is a GSM Protocol) so if you have a CDMA phone (from Sprint etc.) then you should be safe from this flaw as well. We still caution you to always keep your phone up to date and also to avoid any automatic loading of applications or websites.]
Discuss this in our Forum




