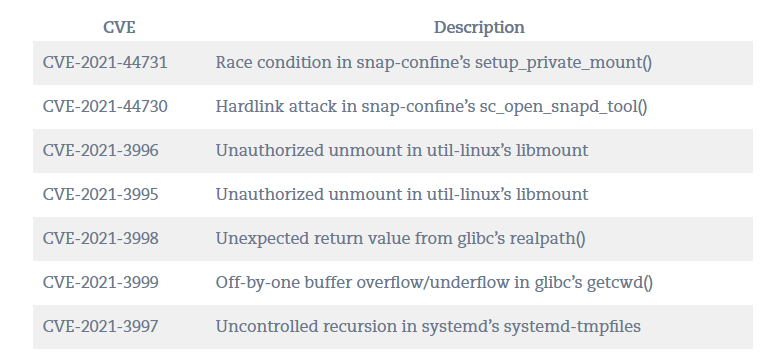
Multiple vulnerabilities were found inside a Linux function called snap-confine by researchers at Qualys. Snap-confine is the function that allows for installation and deployment of packages in Linux. These packages are called snaps and are not specific to any one flavor of Linux. It is a simple method for developers to deliver applications to a wide range of Linux distro directly. The snap service executes the packages in a sandbox that has controlled access to the host where they are executed. Snapd is the name of the tool that runs to effect this, and snap-confine is the name of the sandboxed environment where everything is executed.
One of the vulnerabilities discovered by researchers at Qualys (CVE-2021-44731 named Oh Snap! More Lemmings) is of concern as it allows for a locally logged in unprivileged user to elevate their privileges and execute arbitrary code as root. This is not exactly what you want to hear when you are talking about a core function like this.
Qualys discovered the vulnerability back in October of 2021 and alerted multiple Linux developers as well as Openwall. Form there the public disclosure happened yesterday (02-17-2022) to coincide with the release of patches for the snap-confine vulnerability. Qualys, Ubuntu and Red Hat all advise users to patch as soon as possible. Although the vulnerability is not known to be remotely exploitable it does leave things rather open to compromise to anyone that can log into the target OS. We do wonder if some of the snap API calls could be hijacked to leverage this though).
It is always important to ensure that proper patching is done on systems in a timely manner. Even if it means downtime so that the patches can be properly applied. Leaving vulnerabilities like this open in an OS is just not an option anymore. Security and Operations teams need to work together and have buy in from management to ensure that their organizations are not left open because a vulnerability like this is left in an environment. We also want to stress again, there is no such thing as a secure operating system or cloud service out of the box. You need to take a proactive approach to ensuring security of your endpoints and environment.
Happy patching.