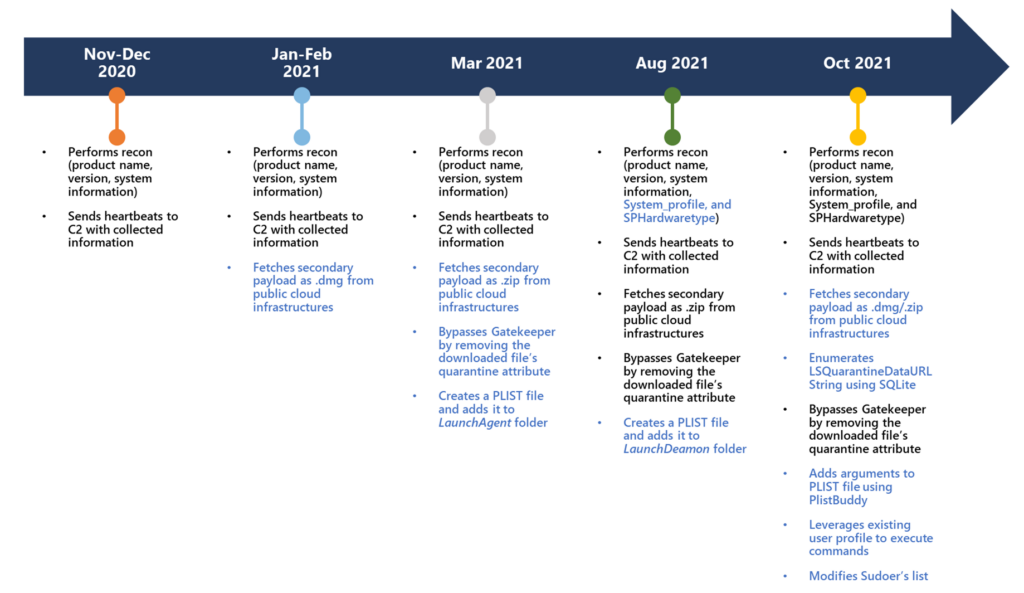
UpdateAgent was first identified in late 2020. Since that time, they have observed an increase in capabilities as well as a refinement in behavior. It also seems that the original creators are still at work on the malware as they are seeing signs of continued development. This is an indication that we can expect more updates and possibly more aggressive impacts to targeted devices. Its most common means of infection are the use of drive-by downloads or malicious ad pop-ups that entice a user to download the malware thinking it is a legitimate piece of software.
UpdateAgent most recent version appears to be focused on the installation of an AdWare tool, AdLoad.
AdLoad is a rather evasive and persistent utility. It can redirect a users’ legitimate web traffic through their own ad servers to inject ads and promotions into web pages and search results. It does this through the installation of a web proxy so that it can control this traffic and collect revenue from the ad displays. AdLoad maintains persistence in a few ways, including being able to download and deploy additional payloads onto an infected system.
Malware like UpdateAgent and AdLoad are serious threats considering what they can do once they gain a foothold on a system. Although, UpdateAgent is focused on macOS, there are other families of malware that target other operating systems in a manner like what we see here. The way the UpdateAgent is being developed is another interesting item. It shows that malware developers can and do continue to evolve their “products” even as they are in use to not only maintain a presence, but also to potentially gain additional access into the systems they infect.
In the case of UpdateAgent things went from information stealing to being able to deploy sophisticated 2nd stage payloads and clean up after themselves as part of the process. It has even been observed removing its own quarantine attribute from Gatekeeper to ensure it remains undetected on an infected system.