The team over at Proofpoint say that DTPacker is not all that new and have observed it used in campaigns going back to 2020. The payloads associated with it tend to be Remote Access Tools (RATs), but they have also identified Keyloggers and other data exfiltration tools in use. DTPacker is used by both APT groups (TA2536 and TA2715) as well as cybercrime organizations. It falls into the commodity malware category meaning it is used in targeted and non-targeted attacks and focus on libraries or software in use across many endpoints (Like MS Office). However, the term commodity has become more and more blurred over the years as APT groups focus on these same libraries and software for their directed attacks as well.
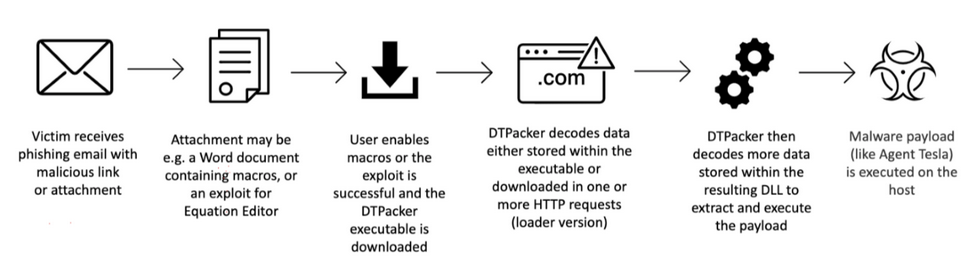
DTpacker is traditionally used in phishing campaigns where the attackers can attach a poisoned word document or another file type with an embedded malicious link. The links often take you to a seemingly benign website but do contain malicious items. Once the user enables macros on the document, DTPacker goes to work. At this point DTPacker can either execute a decoded payload that is embedded or download a payload from an encoded HTTP request. This typically creates a DLL that DTPacker works from.
Stage two of the attack chain is more data decoding from inside the DLL delivered in stage one. The DLL is used to extract and execute the tool that is being pushed. The encoding in both the first stage is varied while the second stage always seems to use the key “Trump2020” or “Trump2026” (this is where the DT comes from). Proofpoint has indicated that they have not seen this in use against political targets, so the name use of this key is just an odd occurrence.
Versions of DTPacker prior to August 2021 used a custom XOR function for decoding which added an interesting level of complexity. After August 2021 new variants were spotted using a straight XOR function. This is also when the new Key Trump2026 showed up.
DTPacker is an interesting addition to an attacker’s tool belt. It is designed for flexibility and obfuscation. From what we can see it should be able to get around some sandboxes, static analysis engines and a few other “slower” legacy detection and response systems. That is not the best news if you are looking to protect against this. Newer EDR solutions that are behavior and math-based stand a much better chance of detecting and stopping this packer. As these newer types of protection monitor a binary through the pre-execution phase to the end of its function, there is a high chance of them catching the RAT, Keylogger or other malicious payload before it gets a chance to be installed. If your new EDR is sophisticated enough, it should also roll back any changes made by DTPacker.
Once again, we see a new technique/tool that leverages weaknesses in MS Office. This is nothing new, but the fact that these campaigns are still successful shows that these weaknesses are still being left open and no proper response tools are in place.