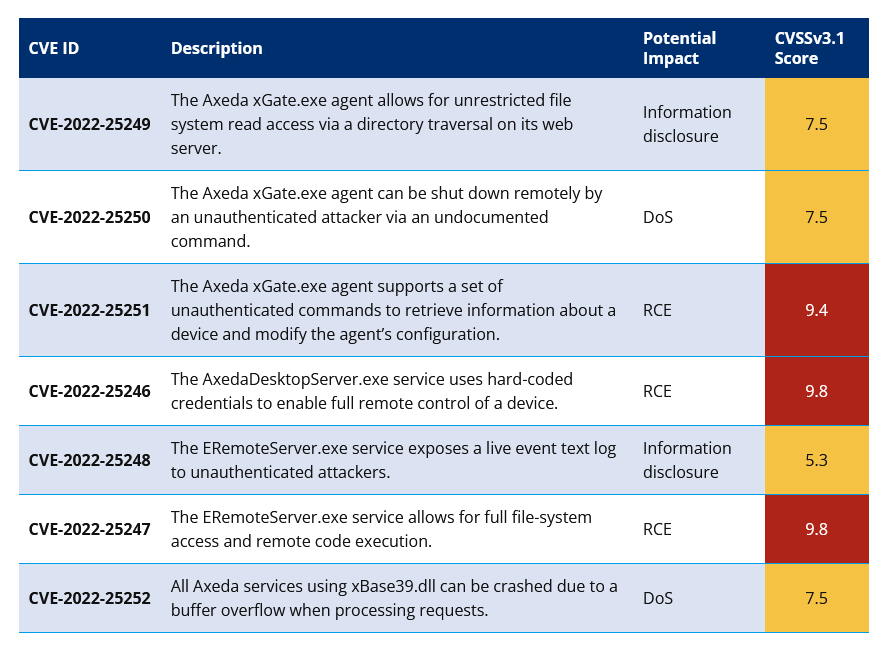
Axeda is a solution that is installed by OEMs which allows remote management of the device after delivery and deployment. According to researchers from Forescout and CyberMDX there are at least 7 vulnerabilities in the 3rd party Axeda software that could allow attackers to compromise devices remotely. The compromises include remote code execution, leaking of sensitive data, stopping/disrupting services. This covers as many as 150 devices from 100 different manufacturers across multiple verticals including healthcare, financial services and manufacturing industries. With more than half of the affected devices in the healthcare industry. The list of devices affected is impressive.
The vulnerabilities exist in all versions of Axeda Agent below 6.9.3. organizations that using Axeda should patch immediately to Agent versions 6.9.1 Build 1046, 6.9.2 Build 1049, or 6.9.3 Build 1051 to remediate the vulnerabilities disclosed.
The Access 7 disclosure is significant in many ways and highlights issues that exist in how devices are not only manufactured but supported. The existence of a third-party agent that is installed and maintained by the OEM is another entry point for an attacker. If the devices are put into an environment without the proper controls (which is likely and may be a condition of support for the devices) the flaws would allow an attacker to get around existing security tools. This is a known issue in many environments where OT (operational technology) devices are in play, yet this type of behavior continues.
Organizations are highly recommended to segment these devices and monitor any and all traffic into and out of them. While these steps do not prevent an attack from happening, they do allow for early detection of compromise and limit an attacker’s lateral movement ability.
Tuesday, 08 March 2022 09:43
Supply Chain Vulnerabilities Found in 150 Devices Spanning Multiple Industries Dubbed Access 7
Written by Sean KalinichReading time is around minutes.
Supply chain attacks are always a concern when it comes to device manufacture and distribution. If an attacker can compromise a part of the supply or management chain, they can affect a large part of the market with relatively minimal effort. The SolarWinds supply chain attack is a perfect example of this type of attack that successfully compromised multiple businesses with only one real “attack”. Now security researchers have disclosed a new group of vulnerabilities in PTC’s Axeda software that allow them to attack the devices after distribution.
Published in
Security Talk
Latest from Sean Kalinich
- ConnectWise Slash and Grab Flaw Once Again Shows the Value of Input Validation We talk to Huntress About its Impact
- Social Manipulation as a Service – When the Bots on Twitter get their Check marks
- To Release or not to Release a PoC or OST That is the Question
- There was an Important Lesson Learned in the LockBit Takedown and it was Not About Threat Groups
- NetSPI’s Offensive Security Offering Leverages Subject Matter Experts to Enhance Pen Testing