From The Blog
-
ConnectWise Slash and Grab Flaw Once Again Shows the Value of Input Validation We talk to Huntress About its Impact
Written by Sean KalinichAlthough the news of the infamous ConnectWise flaw which allowed for the creation of admin accounts is a bit cold, it still is one that…Written on Tuesday, 19 March 2024 12:44 in Security Talk Read 611 times Read more...
-
Social Manipulation as a Service – When the Bots on Twitter get their Check marks
Written by Sean KalinichWhen I started DecryptedTech it was to counter all the crap marketing I saw from component makers. I wanted to prove people with a clean…Written on Monday, 04 March 2024 16:17 in Editorials Read 1517 times Read more...
-
To Release or not to Release a PoC or OST That is the Question
Written by Sean KalinichThere is (and always has been) a debate about the ethics and impact of the release of Proof-of-Concept Exploit for an identified vulnerability and Open-Source…Written on Monday, 26 February 2024 13:05 in Security Talk Read 1066 times Read more...
-
There was an Important Lesson Learned in the LockBit Takedown and it was Not About Threat Groups
Written by Sean KalinichIn what could be called a fantastic move, global law enforcement agencies attacked and took down LockBit’s infrastructure. The day of the event was filled…Written on Thursday, 22 February 2024 12:20 in Security Talk Read 1018 times Read more...
-
NetSPI’s Offensive Security Offering Leverages Subject Matter Experts to Enhance Pen Testing
Written by Sean KalinichBlack Hat 2023 Las Vegas. The term offensive security has always been an interesting one for me. On the surface is brings to mind reaching…Written on Tuesday, 12 September 2023 17:05 in Security Talk Read 2084 times Read more...
-
Black Kite Looks to Offer a Better View of Risk in a Rapidly Changing Threat Landscape
Written by Sean KalinichBlack Hat 2023 – Las Vegas. Risk is an interesting subject and has many different meanings to many different people. For the most part Risk…Written on Tuesday, 12 September 2023 14:56 in Security Talk Read 1801 times Read more...
-
Microsoft Finally Reveals how they Believe a Consumer Signing Key was Stollen
Written by Sean KalinichIn May of 2023 a few sensitive accounts reported to Microsoft that their environments appeared to be compromised. Due to the nature of these accounts,…Written on Thursday, 07 September 2023 14:40 in Security Talk Read 2077 times Read more...
-
Mandiant Releases a Detailed Look at the Campaign Targeting Barracuda Email Security Gateways, I Take a Look at What this all Might Mean
Written by Sean KalinichThe recent attack that leveraged a 0-Day vulnerability to compromise a number of Barracuda Email Security Gateway appliances (physical and virtual, but not cloud) was…Written on Wednesday, 30 August 2023 16:09 in Security Talk Read 2056 times Read more...
-
Threat Groups Return to Targeting Developers in Recent Software Supply Chain Attacks
Written by Sean KalinichThere is a topic of conversation that really needs to be talked about in the open. It is the danger of developer systems (personal and…Written on Wednesday, 30 August 2023 13:29 in Security Talk Read 1833 times Read more...
Recent Comments
- Sean, this is a fantastic review of a beautiful game. I do agree with you… Written by Jacob 2023-05-19 14:17:50 Jedi Survivor – The Quick, Dirty, and Limited Spoilers Review
- Great post. Very interesting read but is the reality we are currently facing. Written by JP 2023-05-03 02:33:53 The Dangers of AI; I Think I Have Seen this Movie Before
- I was wondering if you have tested the microphone audio frequency for the Asus HS-1000W? Written by Maciej 2020-12-18 14:09:33 Asus HS-1000W wireless headset impresses us in the lab
- Thanks for review. I appreciate hearing from a real pro as opposed to the blogger… Written by Keith 2019-06-18 04:22:36 The Red Hydrogen One, Possibly One of the Most “misunderstood” Phones Out
- Have yet to see the real impact but in the consumer segment, ryzen series are… Written by sushant 2018-12-23 10:12:12 AMD’s 11-year journey to relevance gets an epic finish.
Most Read
- Microsoft Fail - Start Button Back in Windows 8.1 But No Start Menu Written on Thursday, 30 May 2013 15:33 in News Be the first to comment! Read 116474 times Read more...
- We take a look at the NETGEAR ProSafe WNDAP360 Dual-Band Wireless Access Point Written on Saturday, 07 April 2012 00:17 in Pro Storage and Networking Be the first to comment! Read 87393 times Read more...
- Synology DS1512+ Five-Bay NAS Performance Review Written on Tuesday, 12 June 2012 20:31 in Pro Storage and Networking Be the first to comment! Read 81936 times Read more...
- Gigabyte G1.Sniper M3 Design And Feature Review Written on Sunday, 19 August 2012 22:35 in Enthusiast Motherboards Be the first to comment! Read 80260 times Read more...
- The Asus P8Z77-M Pro Brings Exceptional Performance and Value to the Lab Written on Monday, 23 April 2012 13:02 in Consumer Motherboards Be the first to comment! Read 70894 times Read more...
Displaying items by tag: CISPA
"National Secutity" Efforts Now Having a Measurable Impact on Public Discourse as Sites Like Gorklaw Close
 |
The fight for internet freedom, privacy and net neutrality has been a rough one. Over the past couple of years we have watched as a parade of laws have trotted past us. SOPA, PIPA, CISPA, and more have all shown us one certain thing; the powers that be have little to no regard for individual freedoms, free speech or the impact of restrictive laws on innovation, technology and the economy as a whole. However there was an underlying trend to these laws that disturbed us and many other privacy and right groups out there. The trend was a general trammeling of the right to free speech when it comes to any online sources; some would even say any source that had an opposing view point. Even the right to have protected sources was slowly being removed if you were an independent blogger (citizen journalist) and this effort is now being expanded.
Technology And The Cloud Helped To Make PRISM Possible
 |
Over the last couple of weeks the new has been flooded with articles about the US Government’s surveillance program called PRISM. It is possibly one of the largest invasions of privacy that has been leaked to the general public. What makes this program all the more concerning is that the NSA appears to have cooperation from each of the companies involved. This apparent breach of consumer trust has caused quite a stir and almost all of the companies that were shown in the leaked power point about PRISM have released statements claiming they only cooperate within the limits of the law. This raises an interesting question though; if a broad request is approved by the Foreign Intelligence Surveillance Court wouldn’t a company be within the law to grant access?
The FBI and Others Want To Fine Companies that Do Not Put in Backdoors.
 |
The FBI and a few other groups would like to put a law in place which would allow them to fine companies that refuse to hand over information regardless of the reasons for not choosing to do so. This plan is part of an increasing effort to force companies to share user information with the government. On the surface the idea looks pretty straight forward. Law Enforcement and other Government Agencies want to be able to track down people that might be using the internet and internet communication services to commit crimes. Sounds legit right?
Microsoft cares about your privacy
 |
Microsoft has embarked on a campaign claiming that they are concerned about your privacy on the internet. The campaign is a direct attack at Google who does not have the best track record when it comes to protecting people’s privacy. In fact Google is currently under investigation for establishing policies that violate EU privacy laws. Microsoft is taking advantage of commotion around Google’s privacy problems to try and bring people over to their side. This move, when looked at is as interesting as it is funny.
Anonymous and Others Call for an Internet Black Out on Monday April 22 2013
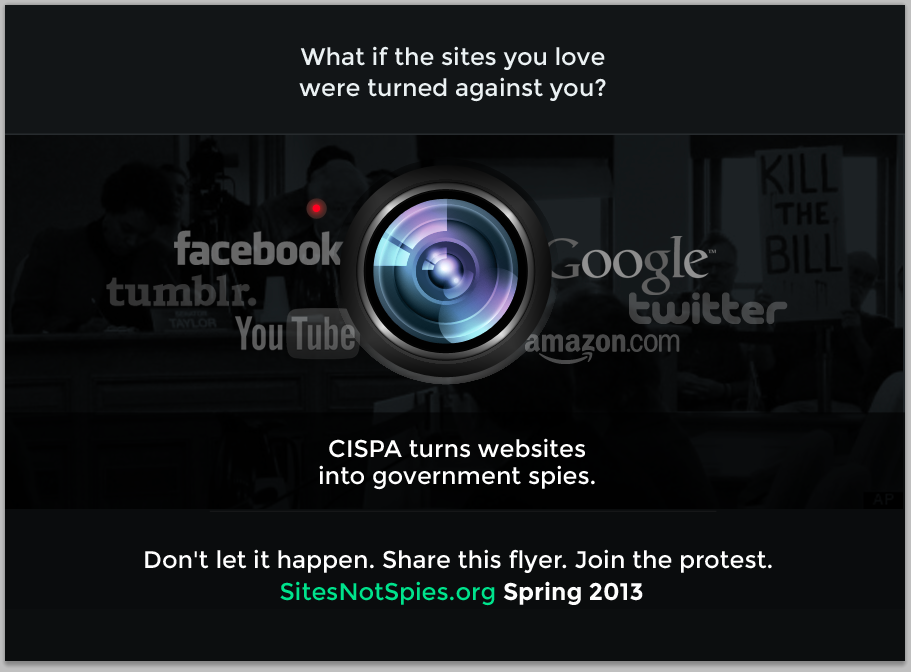 |
As we wrote earlier today the Cyber Intelligence Sharing and Protection Act has passed through the US House of Representatives. This is not an act that anyone, other than the corporations that lobbied for it, wants. CISPA brings nothing to the table that agencies already do not have, or cannot get with the right requests to the courts. Instead it removes many (almost all) individual rights and turns your private data into a commodity that can be passed around without any legal recourse.
Lawmakers want to expand an outdated law... What do they fear?
 |
Over the last few years we have been covering the way that many governments (and corporations) are scrambling to put limitations, controls and other items on the internet. Some of these laws are obvious in their scope like PIPA, SOPA and even CISPA. There is no doubt what these laws are truly intended to accomplish despite the many attempts to paint them as being to protect jobs and national security. However there are other laws that are not as clear and have been passed under the pretense of protecting intellectual property only to be used for other purposes. One of these is the laudable sounding Computer Fraud and Abuse Act.
Does DEA Note leaked to CNET Show a Need for New Laws Or Incompetence?
 |
Remember the news we brought you about the FBI and other law enforcement agencies wanting more power to dig into your electronic communication? Well we have been forwarded an interesting follow on article today that looks like an opening shot in the campaign to get laws passed to extend these powers. The article was published on cnet and raises concerns about what our government is willing to do to get their way and require ISPs to put in real-time monitoring hardware and systems. These systems could potentially allow for broad harvesting of electronic communication without the need for a warrant (if CISPA and other bills are passed as well).
You got a warrant for that?
 |
When I was a little kid I used to watch the cop and spy shows on TV. They were always full of exciting exploits where the good guys always triumphed over the bad buys without ever impugning on their morals. As I grew older the shows started turning more and more dark. The good guy still won, but they were more in the mold of anti-heroes than the white hats I watched a few years ago. The idea of doing morally questionable things in the name of good became more and more popular. Even in books this theme was growing, two one of my favorite fictional characters were very much unethical (yet in some ways moral), one was a criminal, The Stainless Steel Rat, and the other was Elric of Melnibone’ who helped sack his own kingdom to get his Fiancé (there is more to the stories if you want to read them). Now TV and movies are full of this type of “hero” we see them in real life, people who break the law in the name of good. One of the biggest examples of this is the collective known as Anonymous.
National Security Letters Ruled Unconstitutional; Could This Help to Kill CISPA and Other Bills?
 |
An important step for privacy on the internet and actually people’s general right to privacy happened yesterday. Most of us have heard the rumblings of the CISPA (Cyber Intelligence Sharing and Protection Act) and also the Executive Order signed by the US president that allows law enforcement to simply ask for user information. These laws also remove the right to privacy and in some cases the right to anonymity from the public on the internet. What many might not know is that a limited form of these acts has been in effect for some time inside the infamous Patriot Act.
Facebook admits a breach and China gets exposed as the number one Cyber-Threat… again
 |
Over the past year or two we have watched as companies like Microsoft, Crytek, Ubisoft and others push their business model into the cloud. At the same time we have watched as the number of cyber-attacks and data breaches increase. These attacks have also increased in sophistication and in some cases have not been detected until after the breach has been made and data lost. Still companies try to make the claim that their services, out of all of the others, are secure. Simply put (as we have always said) there is no such thing as a secure service, operating system, network or anything else. If it is connected or even powered on it is in danger.
