From The Blog
-
ConnectWise Slash and Grab Flaw Once Again Shows the Value of Input Validation We talk to Huntress About its Impact
Written by Sean KalinichAlthough the news of the infamous ConnectWise flaw which allowed for the creation of admin accounts is a bit cold, it still is one that…Written on Tuesday, 19 March 2024 12:44 in Security Talk Read 604 times Read more...
-
Social Manipulation as a Service – When the Bots on Twitter get their Check marks
Written by Sean KalinichWhen I started DecryptedTech it was to counter all the crap marketing I saw from component makers. I wanted to prove people with a clean…Written on Monday, 04 March 2024 16:17 in Editorials Read 1511 times Read more...
-
To Release or not to Release a PoC or OST That is the Question
Written by Sean KalinichThere is (and always has been) a debate about the ethics and impact of the release of Proof-of-Concept Exploit for an identified vulnerability and Open-Source…Written on Monday, 26 February 2024 13:05 in Security Talk Read 1059 times Read more...
-
There was an Important Lesson Learned in the LockBit Takedown and it was Not About Threat Groups
Written by Sean KalinichIn what could be called a fantastic move, global law enforcement agencies attacked and took down LockBit’s infrastructure. The day of the event was filled…Written on Thursday, 22 February 2024 12:20 in Security Talk Read 910 times Read more...
-
NetSPI’s Offensive Security Offering Leverages Subject Matter Experts to Enhance Pen Testing
Written by Sean KalinichBlack Hat 2023 Las Vegas. The term offensive security has always been an interesting one for me. On the surface is brings to mind reaching…Written on Tuesday, 12 September 2023 17:05 in Security Talk Read 2080 times Read more...
-
Black Kite Looks to Offer a Better View of Risk in a Rapidly Changing Threat Landscape
Written by Sean KalinichBlack Hat 2023 – Las Vegas. Risk is an interesting subject and has many different meanings to many different people. For the most part Risk…Written on Tuesday, 12 September 2023 14:56 in Security Talk Read 1794 times Read more...
-
Microsoft Finally Reveals how they Believe a Consumer Signing Key was Stollen
Written by Sean KalinichIn May of 2023 a few sensitive accounts reported to Microsoft that their environments appeared to be compromised. Due to the nature of these accounts,…Written on Thursday, 07 September 2023 14:40 in Security Talk Read 2067 times Read more...
-
Mandiant Releases a Detailed Look at the Campaign Targeting Barracuda Email Security Gateways, I Take a Look at What this all Might Mean
Written by Sean KalinichThe recent attack that leveraged a 0-Day vulnerability to compromise a number of Barracuda Email Security Gateway appliances (physical and virtual, but not cloud) was…Written on Wednesday, 30 August 2023 16:09 in Security Talk Read 2053 times Read more...
-
Threat Groups Return to Targeting Developers in Recent Software Supply Chain Attacks
Written by Sean KalinichThere is a topic of conversation that really needs to be talked about in the open. It is the danger of developer systems (personal and…Written on Wednesday, 30 August 2023 13:29 in Security Talk Read 1825 times Read more...
Recent Comments
- Sean, this is a fantastic review of a beautiful game. I do agree with you… Written by Jacob 2023-05-19 14:17:50 Jedi Survivor – The Quick, Dirty, and Limited Spoilers Review
- Great post. Very interesting read but is the reality we are currently facing. Written by JP 2023-05-03 02:33:53 The Dangers of AI; I Think I Have Seen this Movie Before
- I was wondering if you have tested the microphone audio frequency for the Asus HS-1000W? Written by Maciej 2020-12-18 14:09:33 Asus HS-1000W wireless headset impresses us in the lab
- Thanks for review. I appreciate hearing from a real pro as opposed to the blogger… Written by Keith 2019-06-18 04:22:36 The Red Hydrogen One, Possibly One of the Most “misunderstood” Phones Out
- Have yet to see the real impact but in the consumer segment, ryzen series are… Written by sushant 2018-12-23 10:12:12 AMD’s 11-year journey to relevance gets an epic finish.
Most Read
- Microsoft Fail - Start Button Back in Windows 8.1 But No Start Menu Written on Thursday, 30 May 2013 15:33 in News Be the first to comment! Read 116471 times Read more...
- We take a look at the NETGEAR ProSafe WNDAP360 Dual-Band Wireless Access Point Written on Saturday, 07 April 2012 00:17 in Pro Storage and Networking Be the first to comment! Read 87377 times Read more...
- Synology DS1512+ Five-Bay NAS Performance Review Written on Tuesday, 12 June 2012 20:31 in Pro Storage and Networking Be the first to comment! Read 81931 times Read more...
- Gigabyte G1.Sniper M3 Design And Feature Review Written on Sunday, 19 August 2012 22:35 in Enthusiast Motherboards Be the first to comment! Read 80251 times Read more...
- The Asus P8Z77-M Pro Brings Exceptional Performance and Value to the Lab Written on Monday, 23 April 2012 13:02 in Consumer Motherboards Be the first to comment! Read 70886 times Read more...
Displaying items by tag: Security
Malformed IFrame Exploit Found In Windows 7 x64 When using Safari
 A new Zero-Day flaw has been found in Microsoft’s Windows 7 OS, but it only applies to a very limited set of circumstances. In this case the system in question needs to be running the 64-bit version of the OS and have Apple’s Safari Browser installed. This combination is probably fairly common as Apple pushes Safari at you with any download of iTunes or QuickTime.
A new Zero-Day flaw has been found in Microsoft’s Windows 7 OS, but it only applies to a very limited set of circumstances. In this case the system in question needs to be running the 64-bit version of the OS and have Apple’s Safari Browser installed. This combination is probably fairly common as Apple pushes Safari at you with any download of iTunes or QuickTime.
CarrierIQ, Not a Keylogger after all
 It looks like the CarrierIQ debacle was quite possibly be a case of Chicken Little meets the digital era with a sinister plot twist. A few weeks ago the news broke that a software researcher (Trevor Eckhart) had found that software that was preinstalled on certain phones appeared to be acting like a keylogger. The hypothesis was based on finding two apps that he could not uninstall or stop. Then he discovered what looked like a link between these two apps and one of the debugging logs (that does record everything that you do). Eckhart announced his findings and a whirlwind of articles ran around the internet a few times.
It looks like the CarrierIQ debacle was quite possibly be a case of Chicken Little meets the digital era with a sinister plot twist. A few weeks ago the news broke that a software researcher (Trevor Eckhart) had found that software that was preinstalled on certain phones appeared to be acting like a keylogger. The hypothesis was based on finding two apps that he could not uninstall or stop. Then he discovered what looked like a link between these two apps and one of the debugging logs (that does record everything that you do). Eckhart announced his findings and a whirlwind of articles ran around the internet a few times.
BSA withdraws support for SOPA
 There are times when you have to wonder what people are thinking. With the SOPA act we wondered that ourselves; especially after a rash of articles came out linking the BSA (Business Software Alliance) to SOPA and by proxy to any member of that group. Now we have never been one to make leaps like that unless we have additional confirmation, but it was enough for use to try and find out what was going on.
There are times when you have to wonder what people are thinking. With the SOPA act we wondered that ourselves; especially after a rash of articles came out linking the BSA (Business Software Alliance) to SOPA and by proxy to any member of that group. Now we have never been one to make leaps like that unless we have additional confirmation, but it was enough for use to try and find out what was going on.
SOPA represents a real threat to Freedom of Information and Speech
 Recent events in Washington have caused quite a stir on the internet as a very oppressive bill is working its way through the legislative branch of the US government. We have talked about this bill and its dangerous consequences more than once but with the release of some new information and after a few questions that we were recently asked we are going to approach it again. First let’s give you a little background as we show you how the US will be if the SOPA (Stop Online Piracy Act) is passed.
Recent events in Washington have caused quite a stir on the internet as a very oppressive bill is working its way through the legislative branch of the US government. We have talked about this bill and its dangerous consequences more than once but with the release of some new information and after a few questions that we were recently asked we are going to approach it again. First let’s give you a little background as we show you how the US will be if the SOPA (Stop Online Piracy Act) is passed.
Infighting Breaks out Inside Anonymous
 Well, you had to know that this day would come. It is something that we have alluded to in some of our coverage of the collective known as Anonymous. It seems that some of the splinter groups inside the larger organization have finally caused enough trouble that Anon is beginning to fight internally. We heard rumors about this a while ago but with no real confirmation we put them aside. Now, however, we find that “Anonymous” has indeed gone after the splinter group known as AnonOps.
Well, you had to know that this day would come. It is something that we have alluded to in some of our coverage of the collective known as Anonymous. It seems that some of the splinter groups inside the larger organization have finally caused enough trouble that Anon is beginning to fight internally. We heard rumors about this a while ago but with no real confirmation we put them aside. Now, however, we find that “Anonymous” has indeed gone after the splinter group known as AnonOps.
Anon calls off OpCartel after Kidnapped Member is Freed
 After going back and forth with on an Op that would have resulted in the release of information on a very violent drug cartel, members of the collective Anonymous have called off their planned OpCartel. They had originally meant to go after this group and release information on members, corrupt police and judges as well as other people that are affiliated with the group (although at the time it was not an official Op yet). Their plans came crashing to a halt when one of their members was kidnapped by the Zetas Drug Cartel.
After going back and forth with on an Op that would have resulted in the release of information on a very violent drug cartel, members of the collective Anonymous have called off their planned OpCartel. They had originally meant to go after this group and release information on members, corrupt police and judges as well as other people that are affiliated with the group (although at the time it was not an official Op yet). Their plans came crashing to a halt when one of their members was kidnapped by the Zetas Drug Cartel.
This incident caused the wavering back and forth as some members wanted to push forward and others were (rightfully) concerned that the kidnapped person would be injured or killed. In the end they decided to move forward and made an announcement that they would release all of the information they had gathered if the kidnapped person was not released.
Earlier today the members of the collective announced that the Anon member had been freed that while he was bruised, he is safe now. In an odd turn the Zeta Cartel released not only the kidnapped member, but also a statement saying that for every name that Anonymous releases that is related to the Cartel they will kill 10 people.
The Zeta Cartel is known as one of the most violent and is also apparently the most technologically savvy groups out there. We have a feeling that while Anonymous does not want to see any innocent blood shed, they will not be leaving the Zetas alone completely. After all, anyone that connects a computer to the internet is at risk from intrusion and they have money and investments in banks that are also vulnerable. I wonder how long it will take before some of those accounts start having balance errors…
Discuss in our Forum
Exploit in Adobe Flash Allows iFrame to Hijack Webcam on Macs
 There is a long standing myth that PCs are susceptible to viruses and malware while Macs and Linux are not. Unfortunately for anyone that believes this myth there are consequences. One of these is a feeling of invulnerability when browsing. This false sense of security can lead to many things, including having your computer hijacked or being silently rolled into a giant Mac only botnet … I am sure you get my point. This phenomenon is not limited to Mac owners. PC owners that have “Full” Virus and Malware protection also get this false sense of security.
There is a long standing myth that PCs are susceptible to viruses and malware while Macs and Linux are not. Unfortunately for anyone that believes this myth there are consequences. One of these is a feeling of invulnerability when browsing. This false sense of security can lead to many things, including having your computer hijacked or being silently rolled into a giant Mac only botnet … I am sure you get my point. This phenomenon is not limited to Mac owners. PC owners that have “Full” Virus and Malware protection also get this false sense of security.
Now, the interesting thing is that while there are literally thousands of viruses and malware for Windows based systems in the wild there are actually more security loop holes in OSX that can be exploited by something as simple as a drive-by or other malformed code on a web page. One that caught our attention was an Adobe based Exploit (yes I know Steve Jobs wanted to ban Adobe). This little exploit allows someone to run a .swf file in a hidden iFrame. The .swf in question here has code to authorize turning on the end users webcam and broadcasting it to the source server.
Now this is nothing new and I have witnessed this kind of thing done at different security conventions. The thing that really is concerning is that this is being run on a version of Flash that is supposed to have code (called frame busting) to prevent this. What happened is that Adobe only patched part of the hole. They covered the whole page being loaded in an iFrame, but forgot to prevent the malformed .swf from being loaded into that same space. This little exploit was found by a computer science student at Stanford University named Feross Aboukhadjeh.
Now I know you are wondering what my rant at the beginning of this article about Macs has to do with this exploit… Well the kicker is that Aboukhadjeh has only been able to get this exploit to work on Macs and running either Firefox or Safari. The reason that he has been so successful is that with these browsers and OSX it is easier to make the iFrame transparent to the end user. Aboukhadjeh says that he does believe that this will work on other operating systems, but that it will take significantly more effort and would require layering the frame to avoid detection.
Adobe has been notified of the exploit
Source The Inquirer
Discuss in our Forum
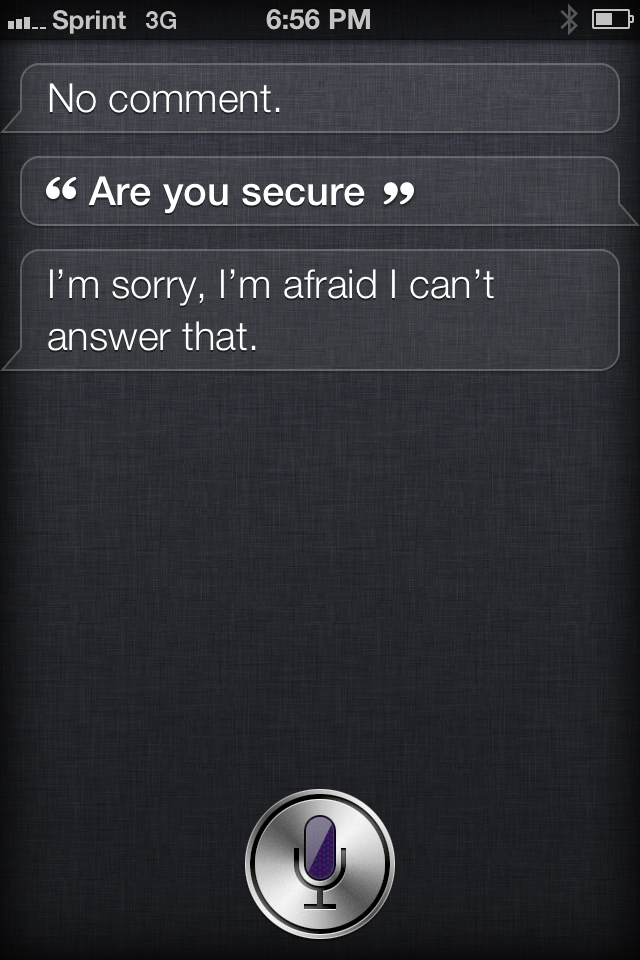
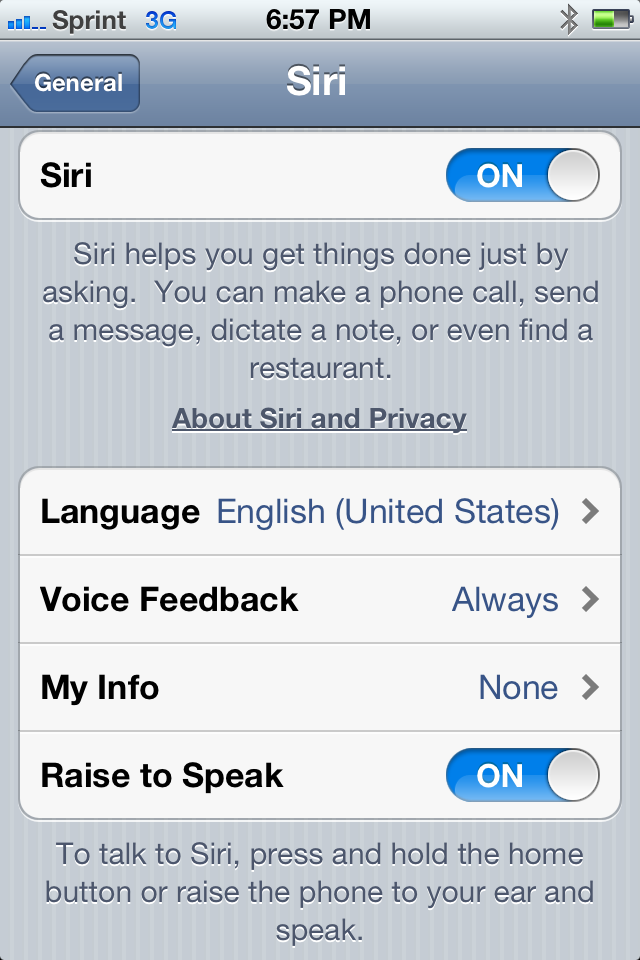
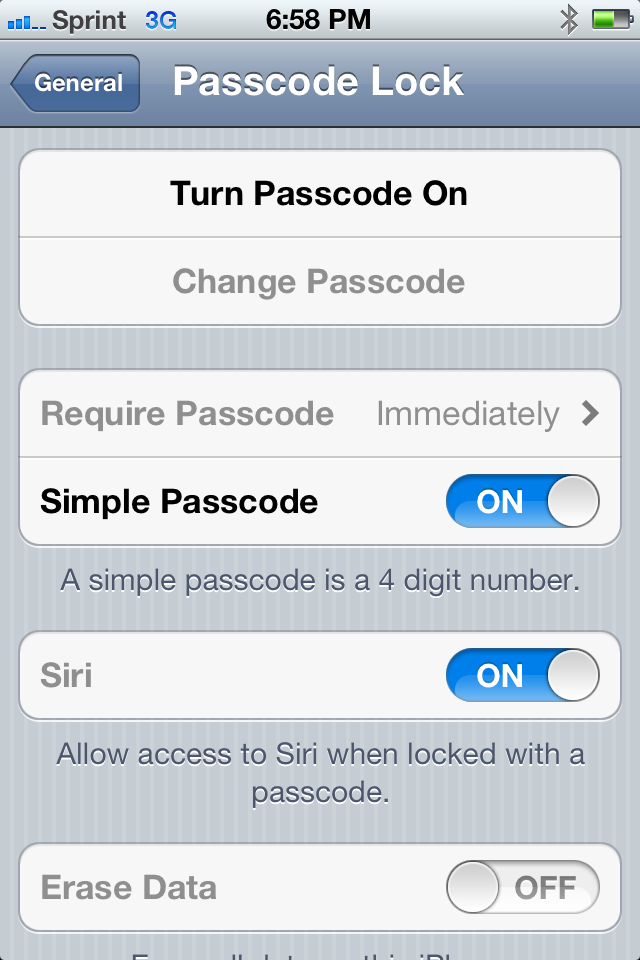
Siri Can Bypass Your Lock Screen
 I am sorry Dave; I can’t let you do that… This line from Stanley Kubrick’s 2001 a Space Oddesy is what came to mind when I showed off this interesting little trick to a friend of mine. While playing around with Siri on their new iPhone 4S we discovered that even when the phone is locked you can send email, text play music, call someone, use the camera and more than a few other things making just about all security useless on the new phone. This is not the first time that security holes have been found on one of Apple’s devices (like finding that the encryption key is stored in plain text on the phone), but I do think this one is one of the funniest.
I am sorry Dave; I can’t let you do that… This line from Stanley Kubrick’s 2001 a Space Oddesy is what came to mind when I showed off this interesting little trick to a friend of mine. While playing around with Siri on their new iPhone 4S we discovered that even when the phone is locked you can send email, text play music, call someone, use the camera and more than a few other things making just about all security useless on the new phone. This is not the first time that security holes have been found on one of Apple’s devices (like finding that the encryption key is stored in plain text on the phone), but I do think this one is one of the funniest.
With all the furor and excitement over what is not much more than a speech to text engine that can run queries against predefined commands to find out that those commands appear to be able to bypass the lock security. What’s more is that Apple allows this by default. I would think that this would not be something that you would want open on a phone with a passcode; however Apple seems to think they know what is best for their customers. I will say this, at least you can turn this feature off, I just think it should have been off already…
 |
 |
 |
For those of you out there thinking about corporate data and email, I have a feeling that Microsoft will add a new security feature into their corporate phone requirements making it impossible to have this running with the lock requirements. I wonder what that will look like…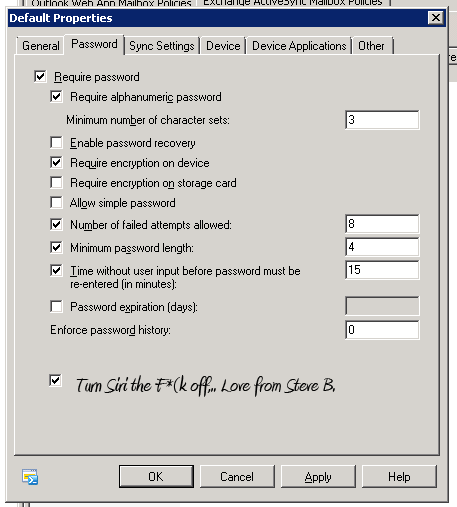
Discuss this in our forum
New Malware Found with Stuxnet Similarities
 Just in case all of the warnings that we gave you before about SCDA (Supervisory Control and Data Acquisition) devices and how insecure most of them are was not enough. We now find that a new piece of malware that appears to be intended spy on industrial networks as a precursor to a future attack like the Stuxnet malware that hit last year. Dubbed Duqu because of a prefix attached to files the new malware creates this new bit of code is very concerning to security experts.
Just in case all of the warnings that we gave you before about SCDA (Supervisory Control and Data Acquisition) devices and how insecure most of them are was not enough. We now find that a new piece of malware that appears to be intended spy on industrial networks as a precursor to a future attack like the Stuxnet malware that hit last year. Dubbed Duqu because of a prefix attached to files the new malware creates this new bit of code is very concerning to security experts.
The code was found on several Windows based systems across multiple companies in Europe. These companies were not directly identified but all appear to have connections to industries that directly interact with basic infrastructure services. As of right now Duqu appears content to just gather information and report back to its command and control servers (including using an internal key logger). Duqu also appears to be sending JPG files back and forth between the server and the infected system, but as many found out to their dismay you can embed quite a bit of information in a JPG files so these could be used to send control instructions and responses or could be nothing more than test files right now.
So far researchers are at a loss as to what Duqu is collecting and why this is happening. They do know that the attacks have been going on since at least December 2010 and that the first variant identified used a stolen certificate much like the original Stuxnet did. Researchers at Symantec and McAfee also feel that the creators of this code had access to the source code of Stuxnet as the two pieces of Malware are very similar in the way they operate and the coding used. Both McAfee and Symantec have also stated that Duqu does not spread and that it does not appear to use any known exploits. This would indicate that the malware uses tactics like drive-by, or social engineering based exploits. These rely on human intervention to download and install the malicious code on a system usually via email or web link.
We personally wonder if this is related to some of the rumors about Anonymous stepping up their attacks on Governments and Large Corporations. After all with what they can gather using some fairly simple techniques (and a nice bit of coding) they can put some rather devastating plans into action very quickly. If this is the case (and this is all just speculation) then we might be looking at an attack that no one is really prepared for. Then again this could all be nothing more than a reconnaissance mission, especially considering the fact that the code uninstalls itself after 30 days…
Source Symantec and McAfee
Discuss this in our Forum
What Google is Missing
 Does anyone check Google + anymore? Well if you do you might have come across a very interesting read today. It seems that one of their developers could no longer contain himself and posted a very telling rant about Google and the way it approaches its products. It seems that Google, despite being a rather large company with many years of experience in cataloging what people do on the internet still has not realized why other companies are more successful than they are.
Does anyone check Google + anymore? Well if you do you might have come across a very interesting read today. It seems that one of their developers could no longer contain himself and posted a very telling rant about Google and the way it approaches its products. It seems that Google, despite being a rather large company with many years of experience in cataloging what people do on the internet still has not realized why other companies are more successful than they are.
I am not talking about search; although I am not a fan of Google’s search and retention practices I will admit they are one of the best search and ad companies out there. I am talking about their other products. Products like Google Docs, Google Chrome, and Google+. The problem is, according to the rant, that Google made each of these as a knee jerk reaction. They were not planned to integrate into a larger platform, they were not designed with user accessibility in mind. They were just built and shoved out the door.
You simply cannot do that in today’s market. You have to plan everything as an integrated approach. If you want a couple of examples then take a look at Microsoft’s Office or the way Apple integrates their OS. To put it bluntly neither Google Docs nor Google + has this. Here is a great quote from the rant to tell you what I mean.
“We had no API at all at launch, and last I checked, we had one measly API call. One of the team members marched in and told me about it when they launched, and I asked: "So is it the Stalker API?" She got all glum and said "Yeah." I mean, I was joking, but no... the only API call we offer is to get someone's stream. So I guess the joke was on me.”
This is a great case in point, there is nothing that can work with or talk to Google+. Even the Google+ link on most sites will work about half the time, or requires constant updating to remain functional. This is because there is no service based platform to run these APIs on, the product just IS.
I have a feeling that this has also extended over into Google’s mobile space and would go a long way to explaining why there are so many issues with Android that seem to remain despite updates. The lack of understanding accessibility and a platform based approach has led Android’s slow acceptance in the tablet market space. The product simply feels like a bigger version of the phone OS and still has many basic apps that are not as sophisticated as the ones that come on the phones (mail is one that comes to mind).
Google as a company is in no danger of going away or going under, however they could find that many of their products will get swept away by other companies that understand accessibility and the need for a common platform better than Google does.
Discuss in our Forum
