Displaying items by tag: Black Hat
Hacker Summer Camp 2023 Recap and My Thoughts
Las Vegas – So Black Hat 2023 and Def Con 31 have come and gone, and while the exhaustion that comes from this epic combined event might not be completely gone, I am ready to give my thoughts on the events. Before I get started, understand that this is my personal opinion on the show(s) as well as my general takeaways from them. As always, your milage may vary. Either way, I hope that you enjoy the article below and that your time and camp this year was amazing (mine was). So, let’s get started!
Illusive Networks says that deception everywhere is the way to go
Black Hat 2017, Las Vegas, NV -
When an attacker gains a foothold in a network the first thing they need to do is learn the lay of the land. They have done some research on the target to gather information about possible systems they might encounter. In reality, they do not truly know what is going on. They are likely to have hit an exposed system with little true access into the good parts of the network. They are going to need to check shares, network connections and also scrape memory for and stored credentials. With these in had they begin the process of moving around the network and building their map of the target environment.
CloudPassage Looks to secure your entire cloud infrastructure
Black Hat 2017, Las Vegas, NV -
The cloud has become one of those buzz words that people like to use when they want you to put your data or workloads on someone else’s computers and network. Amazon Web Services (AWS), Microsoft Azure, and some lesser known systems. The problem is that once you put your information into their network there is a lot that you have to do to ensure that your information or workloads are secure. Amazon, Microsoft and others are only going to take security so far for you and that leave you vulnerable.
If the barbarians are past the gates how do you protect your data from being looted? enSilo says they have a way
The one common thing that I keep hearing everyone talk about at Black Hat and even DEF CON is how to protect your data. It is pretty much a given that if someone wants to get into your network they are going to get in. The number of flaws, vulnerabilities and compromises that are out there are simply too many to protect against. So there needs to be some other method to make sure that any sensitive data that you have is keep out of the hands of the “bad guys”. There are many suggestions about this, but most of them still try to do the same things stop the barbarians at the gate.
With the trend of hacking Encryption,Certs and Keys; how do you really know who to trust?
Have you ever lost your keys and had that moment of panic where you are not sure who might have them? This is not a good feeling. You do not know if someone has them and might use them to gain access to your things. This is the same feeling that should be running through the minds of every IT security professional right now when they think about their certificates and keys, but sadly this is just not happening. The reason that there is not more concern is that far too many even realize just how vulnerable they are.
Welcome to Black Hat and DEF CON 2014
We are on the ground in Las Vegas, NV to cover Black Hat and DEF CON 2014. We will be bringing you coverage of the latest in hacks, exploits and the tools that are supposed to protect you from the “bad guys”. We also brought along some fun toys that are perfect to travel security. Granted nothing we brought it going to keep you 100% safe, but in the real world every little bit helps.
Apple iOS Devices Can Be Infected By USB While the DoJ Shows Apple Knew What It Was Doing With Price Fixing
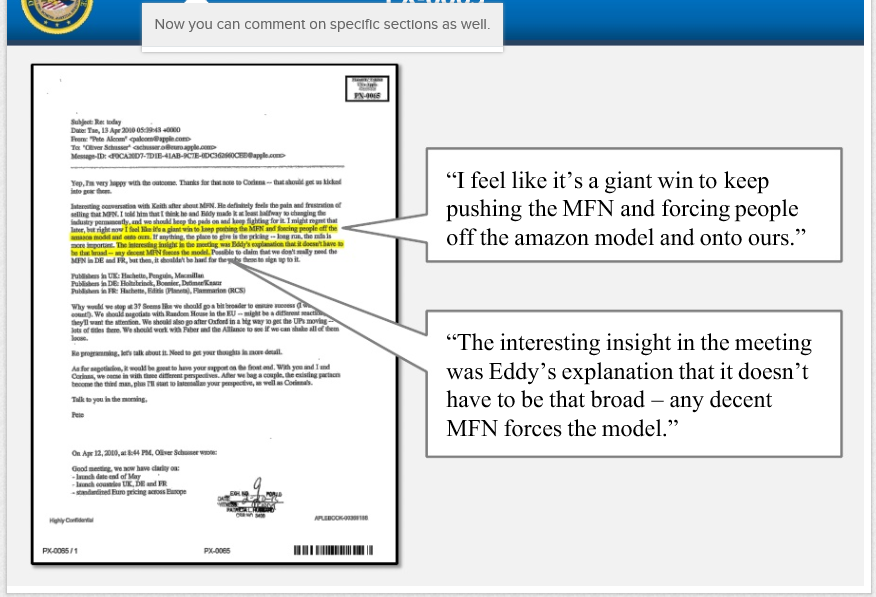 |
For those of you out there that might be laboring under the illusion that Apple products are safe and secure we have some bad news for you. Someone has developed a method of poisoning iPhones, iPads, iPods, well basically anything running iOS, through the use of their charging systems. This means that someone could sell you a compromised charger and take over your phone. This type of attack is hardware based and is almost impossible to get rid of; simply resetting the phone is not going to do it. This is also not the first time that someone has used Apple hardware to create a persistent infection. Not all that long ago someone showed how easy it was to infect the batteries on the MacBook and MacBook Pro. Even the Apple Bluetooth keyboard has been used to slip malware into Apple products.
Anonymous Turns On Hacker That Defaced Children's Charity Site RedSky.tv
 |
Although to many the Anonymous collective is anything but a protector or a hero there are many times when the faceless group has come to the aid of others and punished members (or people pretending to be members) of the group. Although we have heard of more than a few of these internal disciplinary actions, there are a few that stand out. One recent incident was when someone who claimed to be part of Anonymous hacked Sesame Street’s YouTube account and replaced a few Videos with Porn. Another was when a group released names and addresses of police informants and also home addresses for police officers to the public. In both of these cases the guilty parties found themselves on the wrong end of a collective that knows how to not only find you, but make you feel very helpless indeed.
Black Hat Conference Shows Vulnerabilites in Third Party Apps for Apple's iOS
 |
Straight from the Black Hat Conference in Las Vegas we have some bad news for the Apple fans. It seems that the myth surrounding the security of the iPhone is starting to crack around the edges. This is something that we predicted would happen when the trend to use Smartphones for common net tasks first started appearing. It only make sense that malicious coders would start hitting out smart phones after all. I mean how many people use their phones for banking, personal and work email, store passwords to online accounts in their phones with password lockers and more. To be honest, considering the number of smart phones in use, we are surprised that it has taken this long.
OSX Networks are insecure
 As the Black Hat security conference is going on this week we will be covering a lot of the exploits they find. We have already talked about the SCDA vulnerability, how cars with remote lock/unlock/start are vulnerable and even touched in HTML5 and mobile phone exploits. Now we hear confirmation of something we have known for a while: Apple’s OSX server is not secure.
As the Black Hat security conference is going on this week we will be covering a lot of the exploits they find. We have already talked about the SCDA vulnerability, how cars with remote lock/unlock/start are vulnerable and even touched in HTML5 and mobile phone exploits. Now we hear confirmation of something we have known for a while: Apple’s OSX server is not secure.
Experts at the security firm Isec have shown that while individual systems can be secured (the called them islands) once you put the OSX server in play it is “two notches above trivial” to compromise the whole network. Isec showed this off by executing a local DNS exploit that allowed them to scavenge admin credentials and then gain full admin access to the network.
All was not bad news for Apple fans; Isec also said that OSX Lion now “matches” Microsoft’s Windows 7 for local permissions elevation protection and anti-exploit protection. Isec also went on to say that Apple’s marketing has been training consumers to feel safe when using Macs which actually makes them more likely to be open to targeted attacks.



