From The Blog
-
ConnectWise Slash and Grab Flaw Once Again Shows the Value of Input Validation We talk to Huntress About its Impact
Written by Sean KalinichAlthough the news of the infamous ConnectWise flaw which allowed for the creation of admin accounts is a bit cold, it still is one that…Written on Tuesday, 19 March 2024 12:44 in Security Talk Read 715 times Read more...
-
Social Manipulation as a Service – When the Bots on Twitter get their Check marks
Written by Sean KalinichWhen I started DecryptedTech it was to counter all the crap marketing I saw from component makers. I wanted to prove people with a clean…Written on Monday, 04 March 2024 16:17 in Editorials Read 1590 times Read more...
-
To Release or not to Release a PoC or OST That is the Question
Written by Sean KalinichThere is (and always has been) a debate about the ethics and impact of the release of Proof-of-Concept Exploit for an identified vulnerability and Open-Source…Written on Monday, 26 February 2024 13:05 in Security Talk Read 1125 times Read more...
-
There was an Important Lesson Learned in the LockBit Takedown and it was Not About Threat Groups
Written by Sean KalinichIn what could be called a fantastic move, global law enforcement agencies attacked and took down LockBit’s infrastructure. The day of the event was filled…Written on Thursday, 22 February 2024 12:20 in Security Talk Read 1100 times Read more...
-
NetSPI’s Offensive Security Offering Leverages Subject Matter Experts to Enhance Pen Testing
Written by Sean KalinichBlack Hat 2023 Las Vegas. The term offensive security has always been an interesting one for me. On the surface is brings to mind reaching…Written on Tuesday, 12 September 2023 17:05 in Security Talk Read 2144 times Read more...
-
Black Kite Looks to Offer a Better View of Risk in a Rapidly Changing Threat Landscape
Written by Sean KalinichBlack Hat 2023 – Las Vegas. Risk is an interesting subject and has many different meanings to many different people. For the most part Risk…Written on Tuesday, 12 September 2023 14:56 in Security Talk Read 1870 times Read more...
-
Microsoft Finally Reveals how they Believe a Consumer Signing Key was Stollen
Written by Sean KalinichIn May of 2023 a few sensitive accounts reported to Microsoft that their environments appeared to be compromised. Due to the nature of these accounts,…Written on Thursday, 07 September 2023 14:40 in Security Talk Read 2140 times Read more...
-
Mandiant Releases a Detailed Look at the Campaign Targeting Barracuda Email Security Gateways, I Take a Look at What this all Might Mean
Written by Sean KalinichThe recent attack that leveraged a 0-Day vulnerability to compromise a number of Barracuda Email Security Gateway appliances (physical and virtual, but not cloud) was…Written on Wednesday, 30 August 2023 16:09 in Security Talk Read 2110 times Read more...
-
Threat Groups Return to Targeting Developers in Recent Software Supply Chain Attacks
Written by Sean KalinichThere is a topic of conversation that really needs to be talked about in the open. It is the danger of developer systems (personal and…Written on Wednesday, 30 August 2023 13:29 in Security Talk Read 1903 times Read more...
Recent Comments
- Sean, this is a fantastic review of a beautiful game. I do agree with you… Written by Jacob 2023-05-19 14:17:50 Jedi Survivor – The Quick, Dirty, and Limited Spoilers Review
- Great post. Very interesting read but is the reality we are currently facing. Written by JP 2023-05-03 02:33:53 The Dangers of AI; I Think I Have Seen this Movie Before
- I was wondering if you have tested the microphone audio frequency for the Asus HS-1000W? Written by Maciej 2020-12-18 14:09:33 Asus HS-1000W wireless headset impresses us in the lab
- Thanks for review. I appreciate hearing from a real pro as opposed to the blogger… Written by Keith 2019-06-18 04:22:36 The Red Hydrogen One, Possibly One of the Most “misunderstood” Phones Out
- Have yet to see the real impact but in the consumer segment, ryzen series are… Written by sushant 2018-12-23 10:12:12 AMD’s 11-year journey to relevance gets an epic finish.
Most Read
- Microsoft Fail - Start Button Back in Windows 8.1 But No Start Menu Written on Thursday, 30 May 2013 15:33 in News Be the first to comment! Read 116533 times Read more...
- We take a look at the NETGEAR ProSafe WNDAP360 Dual-Band Wireless Access Point Written on Saturday, 07 April 2012 00:17 in Pro Storage and Networking Be the first to comment! Read 87518 times Read more...
- Synology DS1512+ Five-Bay NAS Performance Review Written on Tuesday, 12 June 2012 20:31 in Pro Storage and Networking Be the first to comment! Read 82058 times Read more...
- Gigabyte G1.Sniper M3 Design And Feature Review Written on Sunday, 19 August 2012 22:35 in Enthusiast Motherboards Be the first to comment! Read 80344 times Read more...
- The Asus P8Z77-M Pro Brings Exceptional Performance and Value to the Lab Written on Monday, 23 April 2012 13:02 in Consumer Motherboards Be the first to comment! Read 71008 times Read more...
Displaying items by tag: Security
Yup, hackers get married and have kids too…
 At Defcon 19 in Las Vegas this year the annual security show launched a new event. Called Defcon Kids the even features young “hackers” that have uncovered exploits, vulnerabilities and other security related items. One of the first to speak this year is a 10-Year Old Girl from California who found an exploit in some mobile games.
At Defcon 19 in Las Vegas this year the annual security show launched a new event. Called Defcon Kids the even features young “hackers” that have uncovered exploits, vulnerabilities and other security related items. One of the first to speak this year is a 10-Year Old Girl from California who found an exploit in some mobile games.
The girl, who goes by the alias CyFi (and who is a Girl Scout as well) found the new exploit because she did not want to wait for certain in-game items to complete in a farming game that she plays. To get around this boring wait she simply moved time along. When she did this it opened up the exploit. Independent researchers have verified her findings, but will not list the games that are affected by this (no will CyFi giving the authors a chance to fix things).
CyFi also said that while many games have cheat prevention systems she found that most can be circumvented with a few simple techniques. The Exploit affects both iOS and Android operating systems and illustrates how developers and security experts alike can miss something simple while overthinking their protections and applications.
Source and Image Cnet
Discuss thus on our Forum
OSX Networks are insecure
 As the Black Hat security conference is going on this week we will be covering a lot of the exploits they find. We have already talked about the SCDA vulnerability, how cars with remote lock/unlock/start are vulnerable and even touched in HTML5 and mobile phone exploits. Now we hear confirmation of something we have known for a while: Apple’s OSX server is not secure.
As the Black Hat security conference is going on this week we will be covering a lot of the exploits they find. We have already talked about the SCDA vulnerability, how cars with remote lock/unlock/start are vulnerable and even touched in HTML5 and mobile phone exploits. Now we hear confirmation of something we have known for a while: Apple’s OSX server is not secure.
Experts at the security firm Isec have shown that while individual systems can be secured (the called them islands) once you put the OSX server in play it is “two notches above trivial” to compromise the whole network. Isec showed this off by executing a local DNS exploit that allowed them to scavenge admin credentials and then gain full admin access to the network.
All was not bad news for Apple fans; Isec also said that OSX Lion now “matches” Microsoft’s Windows 7 for local permissions elevation protection and anti-exploit protection. Isec also went on to say that Apple’s marketing has been training consumers to feel safe when using Macs which actually makes them more likely to be open to targeted attacks.
All our wireless beloing to them...
 Remember how we told you about that some of the world’s most sensitive infrastructure hardware could be vulnerable by simply searching for them on Google? Well now we hear that even your car can be compromised with the right gear, as a group of security experts showed at Black Hat in Las Vegas. By setting up their own GSM network (granted not an easy task) the group was able to unlock and then start a Subaru SUV.
Remember how we told you about that some of the world’s most sensitive infrastructure hardware could be vulnerable by simply searching for them on Google? Well now we hear that even your car can be compromised with the right gear, as a group of security experts showed at Black Hat in Las Vegas. By setting up their own GSM network (granted not an easy task) the group was able to unlock and then start a Subaru SUV.
What they did was to capture authentication messages sent from the control server to the car. Once they had these in hand they were able to send commands to the car using an Android based smart phone and that was pretty much it.
As more and more of the world goes wireless you have to worry about what security is (and can honestly be put) in place to protect from this type of attack. It is not uncommon for banks to run wireless as a backup (that is still open and in a passive state) many security cameras will operate over 3G now as well. With the SCDA vulnerability and one I have recently heard of that affects banking applications on both Android and the iPhone you have to wonder just who is in charge of keeping these things safe?
Source Engadget
Discuss this on our Forum
Hello Pot, My name’s Kettle
 In what has to be humorous to those of us that called this last year (yes I was one of them) it has now come out that HTML5 is more full of holes than your average sieve. According to a study out now it appears that HTML5 opens up some serious risks including allowing malicious code to execute cross-domain APIs, ClickJacking, Frame impersonation and worse. One of the problems is that HTML5 (like many other things from Apple) is not compatible with other standards on the net. Some of the “security” features that exist on to prevent cross scripting and window framing (where you put a frame inside a legitimate window to execute malicious code) are rendered useless by the technology in HTML5.
In what has to be humorous to those of us that called this last year (yes I was one of them) it has now come out that HTML5 is more full of holes than your average sieve. According to a study out now it appears that HTML5 opens up some serious risks including allowing malicious code to execute cross-domain APIs, ClickJacking, Frame impersonation and worse. One of the problems is that HTML5 (like many other things from Apple) is not compatible with other standards on the net. Some of the “security” features that exist on to prevent cross scripting and window framing (where you put a frame inside a legitimate window to execute malicious code) are rendered useless by the technology in HTML5.
Other items that are bundled into the code are vulnerabilities that allow a service to register itself as a content handler without notifying the user, and a caching API that can be skimmed to collect user information (location, time of last visit and possible the actual page visited) in much the same way that Google’s Chrome browser can. In all there are some 50 Vulnerabilities that were listed in the report which is of serious concern considering Apple’s push to put this technology in place. Perhaps Apple feels that they can ignore these and continue on with their charmed life, or that their OS would be impervious to any threats. No matter the cause, considering Steve Jobs’ impassioned rants about Adobe and how their products are security risks it is more than a little amusing.
Source The Inquirer
Talk about this in our Forum
Mobile phones, the new Windows XP
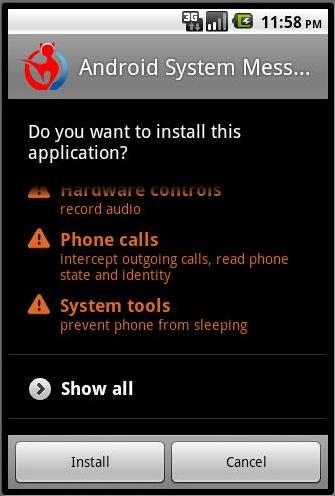 Not that long after Windows XP hit the market a very handy little flaw was found (one of many) that would be the start of a great love/hate relationship with this OS. Even today with Windows XP holding a only a little more than 50% of the PC market the venerable OS accounts for more than 60% of rootkits and something like 80% of the known malware and viruses. What does this have to do with mobile phones? Well is goes something like this; when you buy a mobile phone it comes preinstalled with the OS (usually some derivative of Linux). This OS allows you to setup some rather weak security (a reversible password for screen access). However underneath there are usually two accounts that everything runs on. There is the root account which is the master admin account and has rights to do just about anything. Then there is a mobile user account. This is the account that the UI and all applications run under. The problem? Well every phone out there from each manufacturer uses the same passwords for each (this may actually differ a little between handsets depending on the manufacturer). Yup that is right, if I can guess or hack the root password on one phone; I know them all for that line.
Not that long after Windows XP hit the market a very handy little flaw was found (one of many) that would be the start of a great love/hate relationship with this OS. Even today with Windows XP holding a only a little more than 50% of the PC market the venerable OS accounts for more than 60% of rootkits and something like 80% of the known malware and viruses. What does this have to do with mobile phones? Well is goes something like this; when you buy a mobile phone it comes preinstalled with the OS (usually some derivative of Linux). This OS allows you to setup some rather weak security (a reversible password for screen access). However underneath there are usually two accounts that everything runs on. There is the root account which is the master admin account and has rights to do just about anything. Then there is a mobile user account. This is the account that the UI and all applications run under. The problem? Well every phone out there from each manufacturer uses the same passwords for each (this may actually differ a little between handsets depending on the manufacturer). Yup that is right, if I can guess or hack the root password on one phone; I know them all for that line.
This handy little flaw has been shown on Apple, HTC, Google, Samsung (and just about all Android Phones). Where this becomes important is during application installation. It is during that time that some installers will (or can) access the root account of the phone. If a piece of malware written for your phone OS does this then you can be in a world of trouble.
CA Technologies has been tracking a new brand of malware for the Android platform. It started off by just logging the details of incoming and outgoing calls, but now has moved into actually being able to record these calls and transmit them back to a central server. The days of just installing any app that catches your eye is gone (it never really should have existed anyway). Now more than every Smart Phone users need to be careful what they allow their apps to do. As an extra precaution grabbing a mobile security app like Lookout or Similar for that extra level of protection is a good idea. Just like XP what we think of as secure, turns out to be full of holes after all.
Source and picture CA Technologies
Discuss this in our Forum
You really can find everything on Google
 As the BlackHat conference kicks off in Vegas we hear rumors that some of the global Supervisory Control and Data Acquisition (SCADA) hardware is vulnerable over the internet. Although this is really nothing new what is new is that you can often find this hardware just by running the right searches on Google. According to Tom Parker, CTO at FusionX if you know the right strings and the devices you are looking for either have an embedded webserver or are connected to a system that is connected to the internet then you can send it control commands that can not only operate the equipment but could also cause permanent damage to it. Think of the scene in Die Hard 4 when the “bad guys” sent the commands to open up valves along the natural gas lines. This may sound far-fetched but it is not really.
As the BlackHat conference kicks off in Vegas we hear rumors that some of the global Supervisory Control and Data Acquisition (SCADA) hardware is vulnerable over the internet. Although this is really nothing new what is new is that you can often find this hardware just by running the right searches on Google. According to Tom Parker, CTO at FusionX if you know the right strings and the devices you are looking for either have an embedded webserver or are connected to a system that is connected to the internet then you can send it control commands that can not only operate the equipment but could also cause permanent damage to it. Think of the scene in Die Hard 4 when the “bad guys” sent the commands to open up valves along the natural gas lines. This may sound far-fetched but it is not really.
The problem is that these devices are not sophisticated in the way we think about them. For example one that was used in the presentation is a PLC (Programmable Logic Controller) that they purchased with an embedded webserver (usually for easier operation) with this Parker’s team was able to find certain hardware strings and use Google to identify other PLCs on the internet. One even had a password attached to it. These controllers should never be on the internet as once they are compromised a malicious person (or persons) can wreak havoc on the systems they control.
If you ever wanted a clearer indication that the global infrastructure is vulnerable or that the old school corporate society is ignorant of how the world operates; here it is. We said earlier to imagine Die Hard 4’s “Fire Sale” well in that scenario the hackers had to break into the system; in real life most of the control devices that can be located on the internet are not password protected, use no form of encryption (or simply cannot) and will not work with authentication… Scary when you get right down to it.
Source CNET
Discuss this on our forum
Anon did it!, Well at least that is what you will be told
 Yesterday we were sent a link to some interesting news about a nation-wide crackdown on suspected Anon members. This even included a “hacker” that is fairly close to where I live. The total number of people that were collared was around 15. The FBI and other agencies were very pleased with the day’s activities and went on to say that this was a “major arrest”. However was it really? Do the news or Law Enforcement agencies involved have any clue as to what is really going on? One little indicator that they do not comes up with their timeline; according to most media sources Anon starts as a result of the WikiLeaks incident. However most of the groups involved with Anon pre-date that by many years (in fact Anon does as well).
Yesterday we were sent a link to some interesting news about a nation-wide crackdown on suspected Anon members. This even included a “hacker” that is fairly close to where I live. The total number of people that were collared was around 15. The FBI and other agencies were very pleased with the day’s activities and went on to say that this was a “major arrest”. However was it really? Do the news or Law Enforcement agencies involved have any clue as to what is really going on? One little indicator that they do not comes up with their timeline; according to most media sources Anon starts as a result of the WikiLeaks incident. However most of the groups involved with Anon pre-date that by many years (in fact Anon does as well).
