News
 A rather major, but basic flaw in the way that MySQL and MariaDB handle passwords has opened up both of these to brute force attacks and can allow the attacker to gain access in seconds. This flaw which exploits an issue in the way the passwords are checked using the memcmp function can be used as long as the attacker knows at least one user name. Considering that “root” is almost always in existence the password security on many MySQL and MariaDB databases is practically nonexistent.
A rather major, but basic flaw in the way that MySQL and MariaDB handle passwords has opened up both of these to brute force attacks and can allow the attacker to gain access in seconds. This flaw which exploits an issue in the way the passwords are checked using the memcmp function can be used as long as the attacker knows at least one user name. Considering that “root” is almost always in existence the password security on many MySQL and MariaDB databases is practically nonexistent.
- Details
- By Sean Kalinich
- Hits: 3211
Read more: Password Flaw Leaves Some Versions of MySQL and...
 With all the Apple news yesterday (and filtering over to today) we thought you might like some news about “the other guy” in the mobile race. We are talking about Android her and no, they did not hold a massive dog and pony show. Instead we have a nice and simple announcement from Rock Start games this morning. Max Payne is coming to Android.
With all the Apple news yesterday (and filtering over to today) we thought you might like some news about “the other guy” in the mobile race. We are talking about Android her and no, they did not hold a massive dog and pony show. Instead we have a nice and simple announcement from Rock Start games this morning. Max Payne is coming to Android.
- Details
- By Sean Kalinich
- Hits: 2801
 With all of the security related news flying around we have received word from Kingston about an issue that affects the encryption feature in their SSDNow V+200 and KC100 lines. The issue is with the level of encryption that the SF-2000 is presenting. According to LSI (Pronounce that SandForce) the SF-2000 should be encrypting your data with 256-bit AES encryption. The problem is that it is not providing that and is instead only hitting 128-Bit AES Encryption.
With all of the security related news flying around we have received word from Kingston about an issue that affects the encryption feature in their SSDNow V+200 and KC100 lines. The issue is with the level of encryption that the SF-2000 is presenting. According to LSI (Pronounce that SandForce) the SF-2000 should be encrypting your data with 256-bit AES encryption. The problem is that it is not providing that and is instead only hitting 128-Bit AES Encryption.
- Details
- By Sean Kalinich
- Hits: 3899
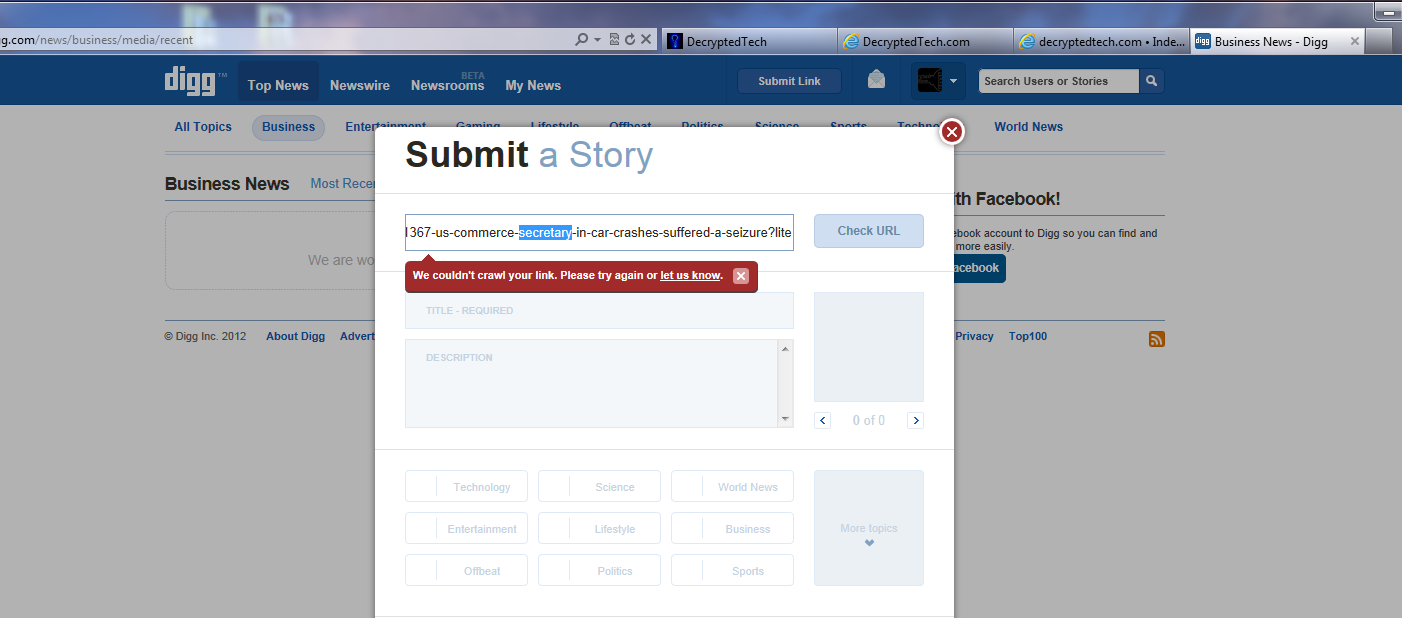 Popular news aggregation site Digg appeared to be having some issues today as it stopped being able to service users. The issue started at around 12:00 Eastern time in the US and at the time of this writing the site is still not available. Upon reaching the site users are greeted with a blank page a simple message saying “No stories found”. ***Updated 6-11-2012 14:51 Digg came back online for around 2 minutes and is back down; still no word as to whatr caused the almost three hour outage****
Popular news aggregation site Digg appeared to be having some issues today as it stopped being able to service users. The issue started at around 12:00 Eastern time in the US and at the time of this writing the site is still not available. Upon reaching the site users are greeted with a blank page a simple message saying “No stories found”. ***Updated 6-11-2012 14:51 Digg came back online for around 2 minutes and is back down; still no word as to whatr caused the almost three hour outage****
***Updated 6-11-2012 19:45 Digg is back online, but still no word on what happened.***
- Details
- By Sean Kalinich
- Hits: 3658
Read more: ***Updated ***News Aggregation Site Digg Seems...
 It would appear that the developers of Stuxnet/Duqu and Flame shared at least some source code during development. At least that is what security research firm Kaspersky seems to think. Kaspersky was the company that found the massive bit of malware that was using a compromised Microsoft Terminal Server licensing model to sign certificates for their code. Flame appears to have been a very coordinated espionage attack on Iran and has been in the news thanks to the complexity and functionality that it has.
It would appear that the developers of Stuxnet/Duqu and Flame shared at least some source code during development. At least that is what security research firm Kaspersky seems to think. Kaspersky was the company that found the massive bit of malware that was using a compromised Microsoft Terminal Server licensing model to sign certificates for their code. Flame appears to have been a very coordinated espionage attack on Iran and has been in the news thanks to the complexity and functionality that it has.
- Details
- By Sean Kalinich
- Hits: 3291
More Articles …
- New Kickstarter Project from Neal Stephenson Pushes For More Realistic Sword Based Games
- US CERT Calls AMD Out For A Security Issue In Their GPU Drivers
- Facebook Rolls Out New 2-Step Mobile Payments System, Could This Be Part of the Phone Development?
- LinkedIn Confirms that Some Passwords Have Been Compromised; Apologizes And Increases Security With Hashing and Salting
Page 507 of 570



