News
 Ok I thought this was pretty cool. While cruising around I stumbled across this hack for the Balance Board that comes with the Nintendo Wii Fit game. It seems some people with a lot more time on their hands than the rest of us (but with some serious brain power) came up with a way to use the Wii Balance board to literally “walk” through Google street view. This inspiration came after a seven hour marathon of modding.
Ok I thought this was pretty cool. While cruising around I stumbled across this hack for the Balance Board that comes with the Nintendo Wii Fit game. It seems some people with a lot more time on their hands than the rest of us (but with some serious brain power) came up with a way to use the Wii Balance board to literally “walk” through Google street view. This inspiration came after a seven hour marathon of modding.
They did have to use OSX and some extra Java applications to communicate back and forth but the end result look very promising. I am willing to bet the Executives at Nintendo are drafting letters and offers as I am typing.
- Details
- By Sean Kalinich
- Hits: 4833
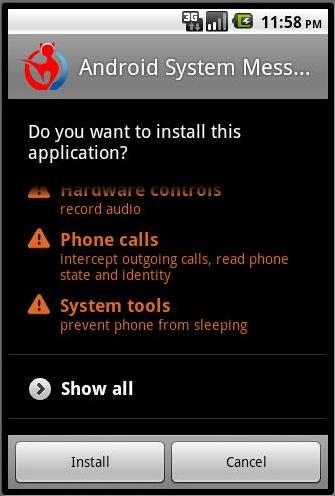 Not that long after Windows XP hit the market a very handy little flaw was found (one of many) that would be the start of a great love/hate relationship with this OS. Even today with Windows XP holding a only a little more than 50% of the PC market the venerable OS accounts for more than 60% of rootkits and something like 80% of the known malware and viruses. What does this have to do with mobile phones? Well is goes something like this; when you buy a mobile phone it comes preinstalled with the OS (usually some derivative of Linux). This OS allows you to setup some rather weak security (a reversible password for screen access). However underneath there are usually two accounts that everything runs on. There is the root account which is the master admin account and has rights to do just about anything. Then there is a mobile user account. This is the account that the UI and all applications run under. The problem? Well every phone out there from each manufacturer uses the same passwords for each (this may actually differ a little between handsets depending on the manufacturer). Yup that is right, if I can guess or hack the root password on one phone; I know them all for that line.
Not that long after Windows XP hit the market a very handy little flaw was found (one of many) that would be the start of a great love/hate relationship with this OS. Even today with Windows XP holding a only a little more than 50% of the PC market the venerable OS accounts for more than 60% of rootkits and something like 80% of the known malware and viruses. What does this have to do with mobile phones? Well is goes something like this; when you buy a mobile phone it comes preinstalled with the OS (usually some derivative of Linux). This OS allows you to setup some rather weak security (a reversible password for screen access). However underneath there are usually two accounts that everything runs on. There is the root account which is the master admin account and has rights to do just about anything. Then there is a mobile user account. This is the account that the UI and all applications run under. The problem? Well every phone out there from each manufacturer uses the same passwords for each (this may actually differ a little between handsets depending on the manufacturer). Yup that is right, if I can guess or hack the root password on one phone; I know them all for that line.
This handy little flaw has been shown on Apple, HTC, Google, Samsung (and just about all Android Phones). Where this becomes important is during application installation. It is during that time that some installers will (or can) access the root account of the phone. If a piece of malware written for your phone OS does this then you can be in a world of trouble.
CA Technologies has been tracking a new brand of malware for the Android platform. It started off by just logging the details of incoming and outgoing calls, but now has moved into actually being able to record these calls and transmit them back to a central server. The days of just installing any app that catches your eye is gone (it never really should have existed anyway). Now more than every Smart Phone users need to be careful what they allow their apps to do. As an extra precaution grabbing a mobile security app like Lookout or Similar for that extra level of protection is a good idea. Just like XP what we think of as secure, turns out to be full of holes after all.
Source and picture CA Technologies
Discuss this in our Forum
- Details
- By Sean Kalinich
- Hits: 2860
 While the corporate world and our governments talk about the dangers of hacker and the evil they represent we find that it is also a favored tool of companies and even new agencies! It was not all that long ago that the US’ anti-consumer RIAA and MPAA were found to have used an investigative firm that employed… let’s say less than legal methods to find file sharers and the files they were offering. They were also found to have improperly accessed these same computer systems and browsed around. Again this is something that was not exactly legal. Now we find that most (if not all) governments employ these same tactics against enemies, allies and even their own citizens.
While the corporate world and our governments talk about the dangers of hacker and the evil they represent we find that it is also a favored tool of companies and even new agencies! It was not all that long ago that the US’ anti-consumer RIAA and MPAA were found to have used an investigative firm that employed… let’s say less than legal methods to find file sharers and the files they were offering. They were also found to have improperly accessed these same computer systems and browsed around. Again this is something that was not exactly legal. Now we find that most (if not all) governments employ these same tactics against enemies, allies and even their own citizens.
One of the funnier news items about corporate hacking comes on the tail of the “New of the World” scandal. It seems that not only did some of their reporters tap phone lines, hound targets of investigation but they also seem to have hired people to hack into some of these target’s computers; one of them an Intelligence Operative in Northern Ireland. It seems that some news agencies, like many corporate entities bent on profit, do not feel the restrictions of ethics.
Source Fudzilla
Discuss this in our Forum
- Details
- By Sean Kalinich
- Hits: 2676
 As the BlackHat conference kicks off in Vegas we hear rumors that some of the global Supervisory Control and Data Acquisition (SCADA) hardware is vulnerable over the internet. Although this is really nothing new what is new is that you can often find this hardware just by running the right searches on Google. According to Tom Parker, CTO at FusionX if you know the right strings and the devices you are looking for either have an embedded webserver or are connected to a system that is connected to the internet then you can send it control commands that can not only operate the equipment but could also cause permanent damage to it. Think of the scene in Die Hard 4 when the “bad guys” sent the commands to open up valves along the natural gas lines. This may sound far-fetched but it is not really.
As the BlackHat conference kicks off in Vegas we hear rumors that some of the global Supervisory Control and Data Acquisition (SCADA) hardware is vulnerable over the internet. Although this is really nothing new what is new is that you can often find this hardware just by running the right searches on Google. According to Tom Parker, CTO at FusionX if you know the right strings and the devices you are looking for either have an embedded webserver or are connected to a system that is connected to the internet then you can send it control commands that can not only operate the equipment but could also cause permanent damage to it. Think of the scene in Die Hard 4 when the “bad guys” sent the commands to open up valves along the natural gas lines. This may sound far-fetched but it is not really.
The problem is that these devices are not sophisticated in the way we think about them. For example one that was used in the presentation is a PLC (Programmable Logic Controller) that they purchased with an embedded webserver (usually for easier operation) with this Parker’s team was able to find certain hardware strings and use Google to identify other PLCs on the internet. One even had a password attached to it. These controllers should never be on the internet as once they are compromised a malicious person (or persons) can wreak havoc on the systems they control.
If you ever wanted a clearer indication that the global infrastructure is vulnerable or that the old school corporate society is ignorant of how the world operates; here it is. We said earlier to imagine Die Hard 4’s “Fire Sale” well in that scenario the hackers had to break into the system; in real life most of the control devices that can be located on the internet are not password protected, use no form of encryption (or simply cannot) and will not work with authentication… Scary when you get right down to it.
Source CNET
Discuss this on our forum
- Details
- By Sean Kalinich
- Hits: 3922
 With AMD’s 8-Core Bulldozer getting ready to hit the streets we now find that we may have a potential price for this new CPU from AMD. According to a contest being held by AMD for fans in the US and Canada the new FX 8150P Bulldozer CPU should go for around $300. This little bit of news popped up on the net after the gang over at insideris.com dug into the announcement of the contest.
With AMD’s 8-Core Bulldozer getting ready to hit the streets we now find that we may have a potential price for this new CPU from AMD. According to a contest being held by AMD for fans in the US and Canada the new FX 8150P Bulldozer CPU should go for around $300. This little bit of news popped up on the net after the gang over at insideris.com dug into the announcement of the contest.
When looking at the contest page (and scrolling down a little) they found that AMD dropped in a line that stated “Top tier prizes: Five (5) AMD FX series eight-core processors. Approximate Retail Value: $300 USD each”. This puts the new 8-Core (Octo-Core) CPU in the same price range as the Intel Core i7 2600k. The question now is, can the Bulldozer keep up with the 2600k? After all we have seen what this CPU is capable of and know that even at stock speeds it is very powerful. We do hope to get one in the lab to find out the answer to this question and you can bet we will be sure to pass this on to you once we find out. For now, I guess we all can speculate and listen to the Intel Vs AMD rhetoric (and secretly get a kick out of it).
- Details
- By Sean Kalinich
- Hits: 3314
More Articles …
Page 565 of 570



