From The Blog
-
ConnectWise Slash and Grab Flaw Once Again Shows the Value of Input Validation We talk to Huntress About its Impact
Written by Sean KalinichAlthough the news of the infamous ConnectWise flaw which allowed for the creation of admin accounts is a bit cold, it still is one that…Written on Tuesday, 19 March 2024 12:44 in Security Talk Read 706 times Read more...
-
Social Manipulation as a Service – When the Bots on Twitter get their Check marks
Written by Sean KalinichWhen I started DecryptedTech it was to counter all the crap marketing I saw from component makers. I wanted to prove people with a clean…Written on Monday, 04 March 2024 16:17 in Editorials Read 1587 times Read more...
-
To Release or not to Release a PoC or OST That is the Question
Written by Sean KalinichThere is (and always has been) a debate about the ethics and impact of the release of Proof-of-Concept Exploit for an identified vulnerability and Open-Source…Written on Monday, 26 February 2024 13:05 in Security Talk Read 1118 times Read more...
-
There was an Important Lesson Learned in the LockBit Takedown and it was Not About Threat Groups
Written by Sean KalinichIn what could be called a fantastic move, global law enforcement agencies attacked and took down LockBit’s infrastructure. The day of the event was filled…Written on Thursday, 22 February 2024 12:20 in Security Talk Read 1089 times Read more...
-
NetSPI’s Offensive Security Offering Leverages Subject Matter Experts to Enhance Pen Testing
Written by Sean KalinichBlack Hat 2023 Las Vegas. The term offensive security has always been an interesting one for me. On the surface is brings to mind reaching…Written on Tuesday, 12 September 2023 17:05 in Security Talk Read 2136 times Read more...
-
Black Kite Looks to Offer a Better View of Risk in a Rapidly Changing Threat Landscape
Written by Sean KalinichBlack Hat 2023 – Las Vegas. Risk is an interesting subject and has many different meanings to many different people. For the most part Risk…Written on Tuesday, 12 September 2023 14:56 in Security Talk Read 1861 times Read more...
-
Microsoft Finally Reveals how they Believe a Consumer Signing Key was Stollen
Written by Sean KalinichIn May of 2023 a few sensitive accounts reported to Microsoft that their environments appeared to be compromised. Due to the nature of these accounts,…Written on Thursday, 07 September 2023 14:40 in Security Talk Read 2134 times Read more...
-
Mandiant Releases a Detailed Look at the Campaign Targeting Barracuda Email Security Gateways, I Take a Look at What this all Might Mean
Written by Sean KalinichThe recent attack that leveraged a 0-Day vulnerability to compromise a number of Barracuda Email Security Gateway appliances (physical and virtual, but not cloud) was…Written on Wednesday, 30 August 2023 16:09 in Security Talk Read 2103 times Read more...
-
Threat Groups Return to Targeting Developers in Recent Software Supply Chain Attacks
Written by Sean KalinichThere is a topic of conversation that really needs to be talked about in the open. It is the danger of developer systems (personal and…Written on Wednesday, 30 August 2023 13:29 in Security Talk Read 1896 times Read more...
Recent Comments
- Sean, this is a fantastic review of a beautiful game. I do agree with you… Written by Jacob 2023-05-19 14:17:50 Jedi Survivor – The Quick, Dirty, and Limited Spoilers Review
- Great post. Very interesting read but is the reality we are currently facing. Written by JP 2023-05-03 02:33:53 The Dangers of AI; I Think I Have Seen this Movie Before
- I was wondering if you have tested the microphone audio frequency for the Asus HS-1000W? Written by Maciej 2020-12-18 14:09:33 Asus HS-1000W wireless headset impresses us in the lab
- Thanks for review. I appreciate hearing from a real pro as opposed to the blogger… Written by Keith 2019-06-18 04:22:36 The Red Hydrogen One, Possibly One of the Most “misunderstood” Phones Out
- Have yet to see the real impact but in the consumer segment, ryzen series are… Written by sushant 2018-12-23 10:12:12 AMD’s 11-year journey to relevance gets an epic finish.
Most Read
- Microsoft Fail - Start Button Back in Windows 8.1 But No Start Menu Written on Thursday, 30 May 2013 15:33 in News Be the first to comment! Read 116532 times Read more...
- We take a look at the NETGEAR ProSafe WNDAP360 Dual-Band Wireless Access Point Written on Saturday, 07 April 2012 00:17 in Pro Storage and Networking Be the first to comment! Read 87503 times Read more...
- Synology DS1512+ Five-Bay NAS Performance Review Written on Tuesday, 12 June 2012 20:31 in Pro Storage and Networking Be the first to comment! Read 82045 times Read more...
- Gigabyte G1.Sniper M3 Design And Feature Review Written on Sunday, 19 August 2012 22:35 in Enthusiast Motherboards Be the first to comment! Read 80342 times Read more...
- The Asus P8Z77-M Pro Brings Exceptional Performance and Value to the Lab Written on Monday, 23 April 2012 13:02 in Consumer Motherboards Be the first to comment! Read 71000 times Read more...
Displaying items by tag: Malware
A Microsoft Engineer Claims There is an Android Botnet; The Proof Is A Little Thin
 Hearing about a flaw in one product from a competitor in a product is sort of like asking your dog what food he likes best. You know you are not going to get a good answer and, of course, the dog is only going to stare at you and eat pretty much anything (including a bug…). So when we heard that a Microsoft Anti-Spam Engineer was reporting a new Android based email spam botnet we took it with a grain of salt (remember Microsoft has a new Phone OS coming out soon).
Hearing about a flaw in one product from a competitor in a product is sort of like asking your dog what food he likes best. You know you are not going to get a good answer and, of course, the dog is only going to stare at you and eat pretty much anything (including a bug…). So when we heard that a Microsoft Anti-Spam Engineer was reporting a new Android based email spam botnet we took it with a grain of salt (remember Microsoft has a new Phone OS coming out soon).
New Tool Called Daedalus Developed By Japan's NICT For Monitoring The "Darknet"
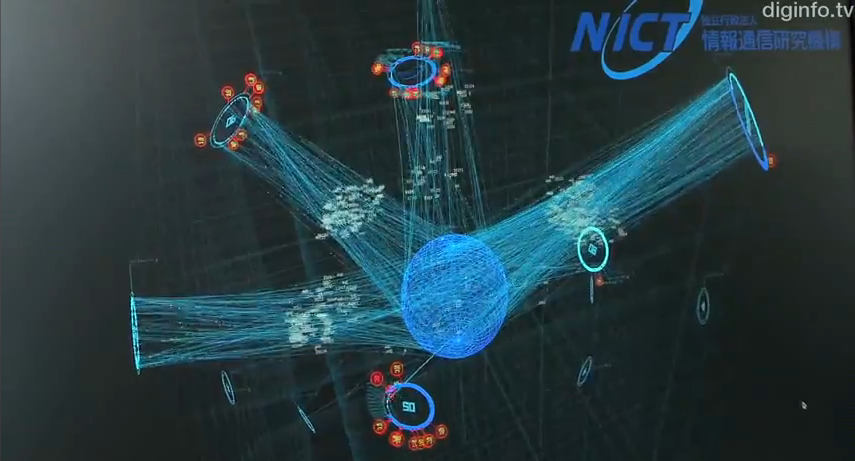 There is an interesting habit in the world of science; when you cannot explain or categorize something add “dark” to the front of the regular word and that makes it all ok. We have seen this in astrophysics, particle physics, theoretical physics, and now to IT. With this maxim we get Dark Matter, Dark Energy and my favorite “Darknet” It just sounds cool right?
There is an interesting habit in the world of science; when you cannot explain or categorize something add “dark” to the front of the regular word and that makes it all ok. We have seen this in astrophysics, particle physics, theoretical physics, and now to IT. With this maxim we get Dark Matter, Dark Energy and my favorite “Darknet” It just sounds cool right?
Flame and Stuxnet Devs Appear to Have Shared Source Code At Least Once
 It would appear that the developers of Stuxnet/Duqu and Flame shared at least some source code during development. At least that is what security research firm Kaspersky seems to think. Kaspersky was the company that found the massive bit of malware that was using a compromised Microsoft Terminal Server licensing model to sign certificates for their code. Flame appears to have been a very coordinated espionage attack on Iran and has been in the news thanks to the complexity and functionality that it has.
It would appear that the developers of Stuxnet/Duqu and Flame shared at least some source code during development. At least that is what security research firm Kaspersky seems to think. Kaspersky was the company that found the massive bit of malware that was using a compromised Microsoft Terminal Server licensing model to sign certificates for their code. Flame appears to have been a very coordinated espionage attack on Iran and has been in the news thanks to the complexity and functionality that it has.
Flame Was Using Subverted Microsoft Certificates To Infect Systems; Microsoft Issues a Patch to Correct This.
 We told you about the new malware threat in Iran (and some other Middle Eastern countries). This is a new and very sophisticated bit of spyware that appears designed to gather intelligence about the state of Iran’s nuclear program. Kaspersky discovered the worm after being asked to check some systems that appeared to be acting strange. This investigation led to the discovery on Flame and the identification of some 20 plug-ins for the malware that can do everything from capture screens, to turning on a system’s microphone to record anything around the system. It is also able to record VoIP communication through applications like Skype.
We told you about the new malware threat in Iran (and some other Middle Eastern countries). This is a new and very sophisticated bit of spyware that appears designed to gather intelligence about the state of Iran’s nuclear program. Kaspersky discovered the worm after being asked to check some systems that appeared to be acting strange. This investigation led to the discovery on Flame and the identification of some 20 plug-ins for the malware that can do everything from capture screens, to turning on a system’s microphone to record anything around the system. It is also able to record VoIP communication through applications like Skype.
New "Backdoor" Security Issue Found With FPGA Chips
 So what is more frightening than having a worm or a virus infect your network? How about a virus or worm that can infect the hardware that controls your network. According researchers at Cambridge this could be possible through the use of hard coded back doors in control processors. Although the idea of being able to reprogram the microcode inside computer chips is nothing new it has never been viewed as a threat before. After all most companies are very careful about allowing someone other than themselves to have access to the paths that would allow the original code to be overwritten.
So what is more frightening than having a worm or a virus infect your network? How about a virus or worm that can infect the hardware that controls your network. According researchers at Cambridge this could be possible through the use of hard coded back doors in control processors. Although the idea of being able to reprogram the microcode inside computer chips is nothing new it has never been viewed as a threat before. After all most companies are very careful about allowing someone other than themselves to have access to the paths that would allow the original code to be overwritten.
Facebook Rolls Out Sponsored Posts... Not Much More than Sponsored Spam Really
 Remember when we told you that Facebook was going to allow companies to pay to promote certain posts? Well it is now in full swing as it looks like Facebook has rolled out the service to everyone’s pages. Over the last week we have been having issues with posting links on the DecryptedTech Facebook page, yet when we reported the issue there was almost no response from Facebook about the issue. As it turns out this issue was due to the changes that Facebook was making behind the scenes.
Remember when we told you that Facebook was going to allow companies to pay to promote certain posts? Well it is now in full swing as it looks like Facebook has rolled out the service to everyone’s pages. Over the last week we have been having issues with posting links on the DecryptedTech Facebook page, yet when we reported the issue there was almost no response from Facebook about the issue. As it turns out this issue was due to the changes that Facebook was making behind the scenes.
Massive "Flame" Cyber Attack Targeted At Some Middle Eastern Countries
 An interesting report has popped up about a rather large attack on a group of Middle Eastern countries. The attack (called Flame) appears to be a targeted attack against Iran, Israel, Palestine, Sudan, Syria, Lebanon, Saudi Arabia and Egypt with the most effected being Iran, Palestine, and Israel. The attack was reported by Kaspersky Labs and looks to be intended to collect all kinds of information (not just data on computers). Kaspersky believes that Flame has been operating for at least two years in this region.
An interesting report has popped up about a rather large attack on a group of Middle Eastern countries. The attack (called Flame) appears to be a targeted attack against Iran, Israel, Palestine, Sudan, Syria, Lebanon, Saudi Arabia and Egypt with the most effected being Iran, Palestine, and Israel. The attack was reported by Kaspersky Labs and looks to be intended to collect all kinds of information (not just data on computers). Kaspersky believes that Flame has been operating for at least two years in this region.
Rich Text Format Flaw Leaves OSX and Windows Vulnerable If Running MS Office
 In the IT world there was a time when we all feared the Marco viruses that could be embedded into Word, Excel and other Microsoft Office Products. It was bad enough at one point that I found a single system with over 3,200 counts of an Excel Macro virus (it replicated itself quite nicely). Back then it was common for IT to recommend the use of RTF (Rich Text Format) instead of .DOC for documents and there was even an option inside exchange to force the use of this format even if the end user has Word as their email editor.
In the IT world there was a time when we all feared the Marco viruses that could be embedded into Word, Excel and other Microsoft Office Products. It was bad enough at one point that I found a single system with over 3,200 counts of an Excel Macro virus (it replicated itself quite nicely). Back then it was common for IT to recommend the use of RTF (Rich Text Format) instead of .DOC for documents and there was even an option inside exchange to force the use of this format even if the end user has Word as their email editor.
More Security Woes for Apple As A New FlashBack Variant Pops Up
 Well, well, well… although we have been saying it ever since the first Macs with Intel CPUs rolled off the lines in the Foxconn factories in China it seems like the world is finally realizing that the Mac IS a PC just running a different OS. The first kick in the head was delivered when the Flashback Malware hit the streets in the form of a fake flash installer which made any infected Mac part of a global botnet.
Well, well, well… although we have been saying it ever since the first Macs with Intel CPUs rolled off the lines in the Foxconn factories in China it seems like the world is finally realizing that the Mac IS a PC just running a different OS. The first kick in the head was delivered when the Flashback Malware hit the streets in the form of a fake flash installer which made any infected Mac part of a global botnet.
400,000+ Still Infected with the Four Year Old DNSChanger Malware; Could Lose Internet on July 8th
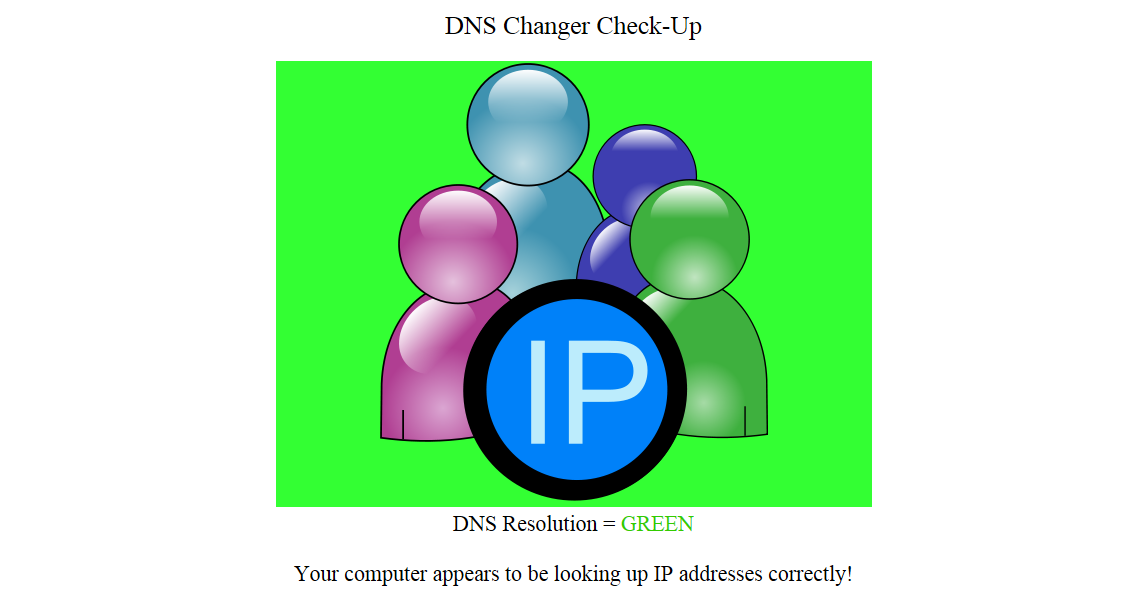 There is a lot of talk in the news about a very old piece of malware. This malicious code was called DNSChanger and was part of a criminal enterprise that intended to route people’s traffic through their own servers instead of the intended servers. This opened the victims up to countless other potential infections. The Malware was discovered back in 2004 and had a small amount of fame for its time. The impact of this particular infection was rated into the millions of Windows based PCs. Although the malware was identified and six people were arrested for it, the authorities did not know what to do about the infected systems (which is VERY odd).
There is a lot of talk in the news about a very old piece of malware. This malicious code was called DNSChanger and was part of a criminal enterprise that intended to route people’s traffic through their own servers instead of the intended servers. This opened the victims up to countless other potential infections. The Malware was discovered back in 2004 and had a small amount of fame for its time. The impact of this particular infection was rated into the millions of Windows based PCs. Although the malware was identified and six people were arrested for it, the authorities did not know what to do about the infected systems (which is VERY odd).
